The man-in-the-middle attack on the 417 is difficult to understand even for control system engineers, since it has never been seen before, and not even thought possible. It’s like a circus stunt where the elephant does a one-armed handstand. Let’s try to explain what happens with some graphics.
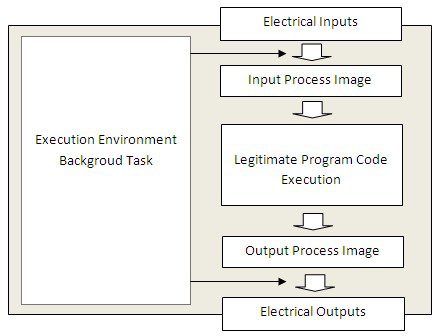
1. Normal operation
In normal PLC operation, the execution environment takes care of moving the electrical inputs to the input process image, and the output process image to the electrical outputs. All this takes place in the background without the user program having to worry about it.
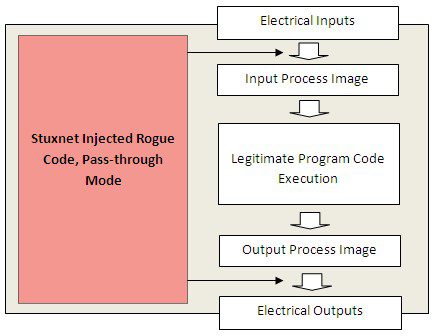
2. Pass-through mode
The funny thing is that you can switch the automated updates off. This is what Stuxnet does. It then takes care of providing the input process image and the electrical outputs for the legitimate program by itself. This takes place in FC 6083, which is called from the main sweep OB 1, since it was injected there by Stuxnet. When we first saw that, we had a hard time making sense out of it because Stuxnet was shifting the images unmodified; it was doing something that would not have been necessary because the execution environment would do it automatically. That is, until you turn that feature off. Execution of OB 1 then takes considerably longer, but Stuxnet takes care about that by having turned off cycle time monitoring.
3. Attack mode
In attack mode, Stuxnet no longer is so friendly to provide the legitimate user code with real input data. Instead, it dumps fake input data to the input process image. In the meantime, it manipulates outputs without the legitimate user program recognizing anything. Note that the following diagram is a little bit simplified for clarification.
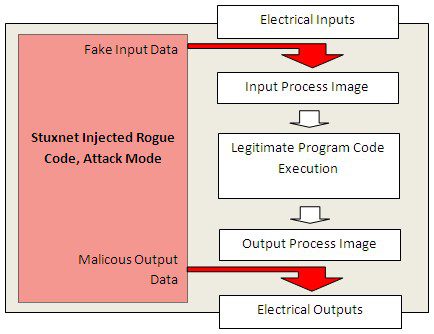
One point worthwhile noting is that Stuxnet does not exploit something like a zero-day vulnerability here. It just makes creative use of legitimate product features that cannot be considered bugs – and cannot be “patched”.
