ICS-CERT advises Siemens S7 users to install intrusion detection systems that feature deep packet inspection of the proprietary S7 protocol, so we thought we give blog readers an idea about what such an IDS might look like. The following highlights some features of our Total Control monitoring solution, a real-world product that’s on the market since 2006.
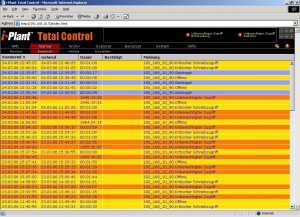
The recommended configuration option for Total Control is to use it as a forward-deployed IDS to monitor network traffic to and from S7 PLCs at the last mile, i.e. within the control system cabinet. Data from multiple IDS sensors can be consolidated at a central server that is accessible via a browser interface. The centerpiece of Total Control is an event log that logs access to monitored controllers, indicating criticality. For example, configuration and ladder logic changes are automatically categorized critical. Even better, manipulations of selected symbolic process variables can also be marked as critical. In order to do that, the administrator can load the symbolic project information from Simatic Manager (the engineering software) to Total Control, giving the IDS the opportunity to map the controller’s memory to symbolic variable names and decode memory content to appropriate numeric or string data types. All fields of the event log can be searched in a database. So for example, queries like “show me the last re-configuration of burner four”, or “show me all manipulations from engineering station six (identified by reverse DNS)”, or “who changed the value of the temperature of boiler two last week” are processed in a matter of seconds.
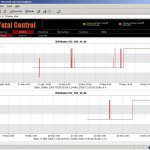
Total Control comes with an integrated alarm messaging system similar to SCADA alarm tables. The administrator gets a quick overview of alarms that can also be automatically forwarded by email or text message. A stock-market ticker like live display of alarms is displayed at the top of the screen for alarms that require operator acknowledgement, such as unauthorized write access to critical systems. As Total Control does full deep packet inspection, write access means actual manipulation of controller configuration or process variables. Polling requests are filtered out. Controller run mode and network availability are also monitored and can be graphically displayed, allowing the user to quickly spot and analyze controller and network downtime.
Last but not least, Total Control features HMI-like system diagrams that can be created with an integrated graphics editor. A system diagram provides the administrator with an intuitive understanding of controller health and potential security events. For example, controller status is updated live, where broken network links can be identified by connection lines changing from green to red, and stopped controllers being depicted by photo-realistic red controller “stop” LEDs. Security alerts such as unauthorized system access are also displayed in realtime.
Is this what DHS had in mind? We think so.