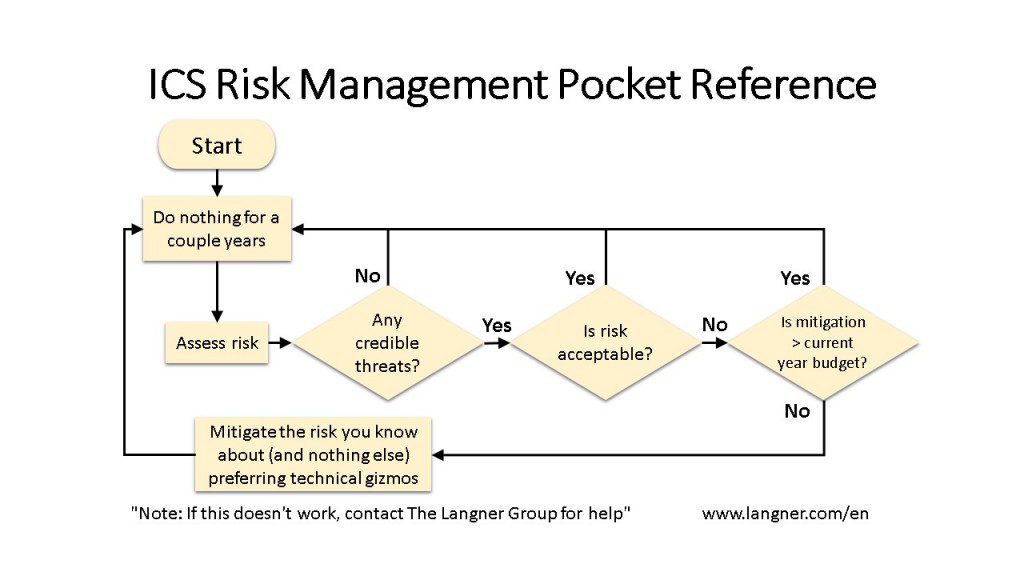
Security practitioners in the field are admonished time and again to manage the risk, yet are left with a bewildering array of risk management philosophies and methodologies to choose from. Every agency or standards body has put their stamp of approval on a particular approach to “risk inform” your process along with the appropriately colorful visual model to show just how this risk model works to manage risk. However, through diligent study and deep technical analysis, some common threads have emerged and the results are presented here in simplified flow chart form for easy digestion.