Earlier we have said that the 417 malcode loads fake data to the input process image and that this would be similar to feeding an observation camera with pre-recorded video. Actually, the analogy holds pretty well. The fake input data is really RECORDED by Stuxnet on the PLC from the original process. It is not static data that would be loaded from the rogue DLL; the recorded data is played back to the legitimate user code which assumes everything is fine and dandy while Stuxnet is manipulating outputs based on real input conditions. So what the legitimate process sees is not fiction but realistic footage; the problem is it has no relation to what is going on at inputs at the same time.
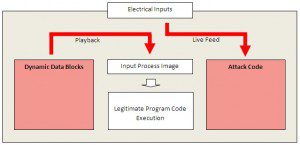
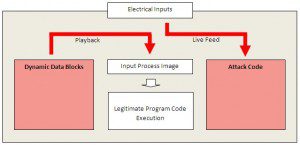
Let’s examine how this works in detail. The following diagram is a more detailed schematic for what happens in pass-through mode.
As can be seen, for periods of time, Stuxnet not only passes electrical inputs through to the input process image, but also records the data in its dynamic data blocks. When the time has come to hit, this recorded data is played back to the process image, while the attack routine works with the real electric inputs.