A good strategy in cyber forensics is to not only look at the code, but also, and predominantly, at the data. Data structures may reveal much more about a cyber attack than code. Just remember the thing with the 6×31 drives in the 315 forensics: It was data and configuration that delivered the most striking evidence, not code. That having said, let’s go back to the 417 attack.
A centrifuge cascade in Natanz consists of 164 centrifuges. However, the individual centrifuges are not piped together in a strict serial fashion. Decades ago, physicists had figured out that cascade performance is increased if multiple centrifuges are connected in parallel within the series. This is then called a cascade stage, or enrichment stage. So while a strictly serial cascade in theory would have 164 stages with only one centrifuge in each stage, an optimized cascade has much less, with multiple centrifuges in each stage, or at least in most stages. In an optimized cascade, a stage with one centrifuge is the exception, which may exist though at the far end of the cascade. All physical parameters given, optimum cascade configuration can be computed, and results in some characteristic belly-shaped curve patterns.
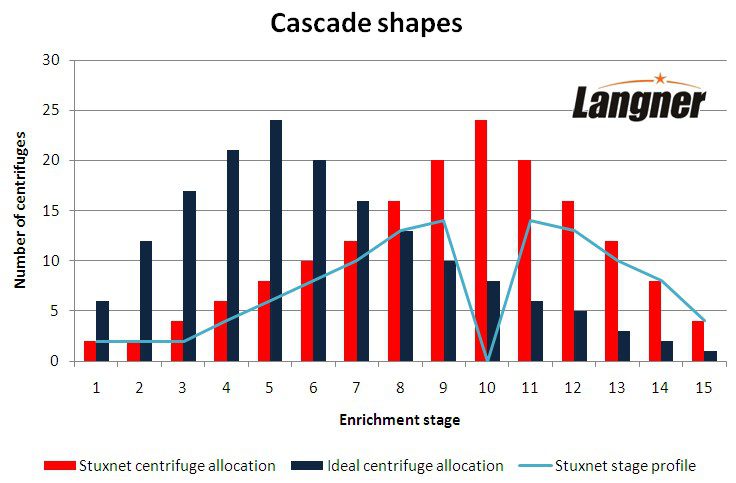
In 2006, Gholam Reza Aqazadeh, the former head of the Iranian nuclear program, was kind enough to inform the public in a TV interview that IR-1 cascades are configured in 15 stages. With some additional information given by Aqazadeh, scientists have been able to calculate the ideal configuration of an IR-1 cascade. In the diagram below, this is what the dark blue bars indicate. Stage one consists of the first six centrifuges, for example, and stage five consists of 24 centrifuges. Stage five is especially noteworthy because that is where the highest number of centrifuges is grouped, which is also the stage where the feed of UF6 takes place. Enriched product from stage five is piped forward to stage six, while waste from stage five is piped back to stage four. Enriched product from stage six is piped forward to stage seven, while waste from stage six is piped back to stage five, et cetera, et cetera.
What you see in red refers to a data structure extracted from actual Stuxnet 417 attack code. It shows how Stuxnet groups centrifuges, individually referenced by numbers from 1 to 164, into stages. In essence, it’s the reverse of the ideal cascade configuration, almost as if a mirror had been used between stage seven and eight. The stage with the highest number of centrifuges (24), for example, is moved from stage five to stage ten.
And then there is a flat integer array with fifteen entries. The values are shown in the cyan line. Looks like there is a big problem in stage ten. This would be consistent with the attack profiles that we have discussed on January 5, where profile one was only spinning up to 24 in stage ten, and dropping back down from there.
References
Brigoli, B.: Cascade theory. In: Villani, S. (Ed.): Uranium enrichment. Springer, Berlin/Heidelberg/New York 1979
Wood, H.G.; Glaser, A.; Kemp, Scott: The gas centrifuge and nuclear weapons proliferation. In: Physics Today, Sept 2008
Glaser, A.: Characteristics of the gas centrifuge for uranium enrichment and their relevance for nuclear weapon proliferation. In: Science and global security, 2008
Credits
Tom Bielefeld (Harvard University) supplied technical background literature