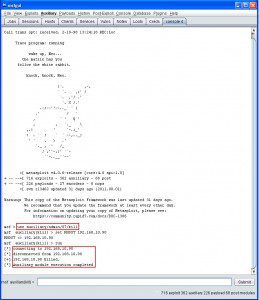
 Joe Weiss asked me to explain low-key controller attacks at his upcoming security conference in DC, such as what we have recently illustrated with our fourteen-byte time bomb. To make the case even more plausible, we implemented a Metasploit module. After execution, the attacked controller is brain-dead, with actuators running wild. More information will be made available at WeissCon.
Joe Weiss asked me to explain low-key controller attacks at his upcoming security conference in DC, such as what we have recently illustrated with our fourteen-byte time bomb. To make the case even more plausible, we implemented a Metasploit module. After execution, the attacked controller is brain-dead, with actuators running wild. More information will be made available at WeissCon.
For a discussion of cyber attack vectors against controllers I recommend everybody to follow Digital Bond’s Project Basecamp.
Ralph Langner
