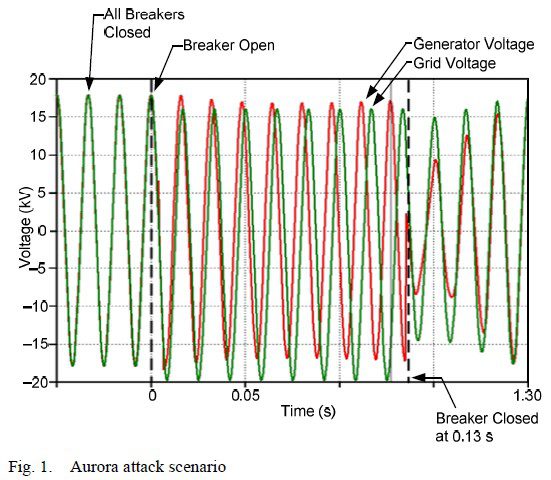
Schweitzer Engineering Labs has published an excellent paper on the Aurora vulnerability, which was originally discovered by DHS/INL in 2007. (Hint for IT folks: This vulnerability is completely unrelated to the attack against Google.) The paper is a must-read for anyone wanting to understand real-world vulnerabilities in automation and control.