It is impossible to overstate the significance of vulnerability management in operational technology (OT). A single vulnerability can cause substantial damage to critical infrastructure and result in significant security breaches. However, managing OT vulnerabilities is not always a simple process. It can be intimidating, especially when performed manually. Therefore, OT vulnerability management must be automated to increase efficiency and effectiveness.
With the appropriate approach, OT vulnerability management can be simplified. It begins with having a complete and up-to-date inventory of assets. This is due to the fact that vulnerabilities impact specific hardware and software products. Therefore, it is essential to understand which products are in use and where they are located. OT asset management software comes in useful in this situation.
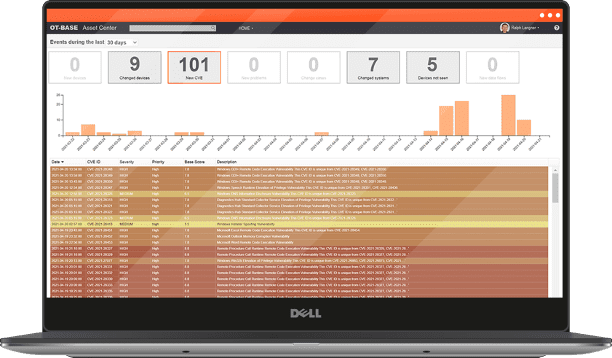
OTbase is one such software that will help effectively manage OT vulnerabilities. It automatically generates an inventory of all network assets and maps them to the 200,000+ CVEs. It would be unfeasible to accomplish this manually. Using this software, you can quickly identify vulnerabilities and rank them according to their level of severity.
OTbase goes above and beyond by informing you of exploitable vulnerabilities. This enables you to prioritize your mitigation efforts in order to resolve the most critical vulnerabilities first. It also identifies devices that pose a greater cyber risk than others, such as those with critical functions or internet access.
Additionally, OTbase can identify software products that significantly increase your cyber risk. For instance, Windows 7 and Adobe Flash Player are known to be susceptible to cyberattacks. You can now plan to upgrade or replace these products to reduce your cyber risk.
Critical to the security and stability of your OT infrastructure is the administration of OT vulnerabilities. It is an ongoing process that requires routine monitoring and updates. OTbase monitors your assets in real-time and automatically refreshes your inventory whenever a new asset is added to your network.
OTbase is also simple to use and set up. It does not require any technical knowledge to operate. The software’s user interface is intuitive, allowing you to manage OT vulnerabilities easily.
Management of OT vulnerabilities should not be treated casually. It requires a complete and up-to-date asset inventory, severity-based prioritization of vulnerabilities, and continuous monitoring and updates. OTbase is a powerful software that can assist you in achieving these objectives and more. You can be certain that your OT infrastructure is secure and protected due to its real-time monitoring, automatic updates, and user-friendly interface. Why not give OTbase a try today and take the first step toward effective OT vulnerability management?
Learn more about OTbase.
There are around 30+ products in the “ICS Detection” category, but OTbase isn’t one of them. You may have a hard time understanding how one ICS Detection product differs from the next, but it’s easy to see how OTbase differs from all of those. For a quick check if it could be the right product for your company’s journey toward efficient OT asset management, book a meeting with our experts for more background.