Resources

Latest blog posts
From IP Addresses to Actionable Intelligence: The Power of a Contextualized OT Asset Inventory
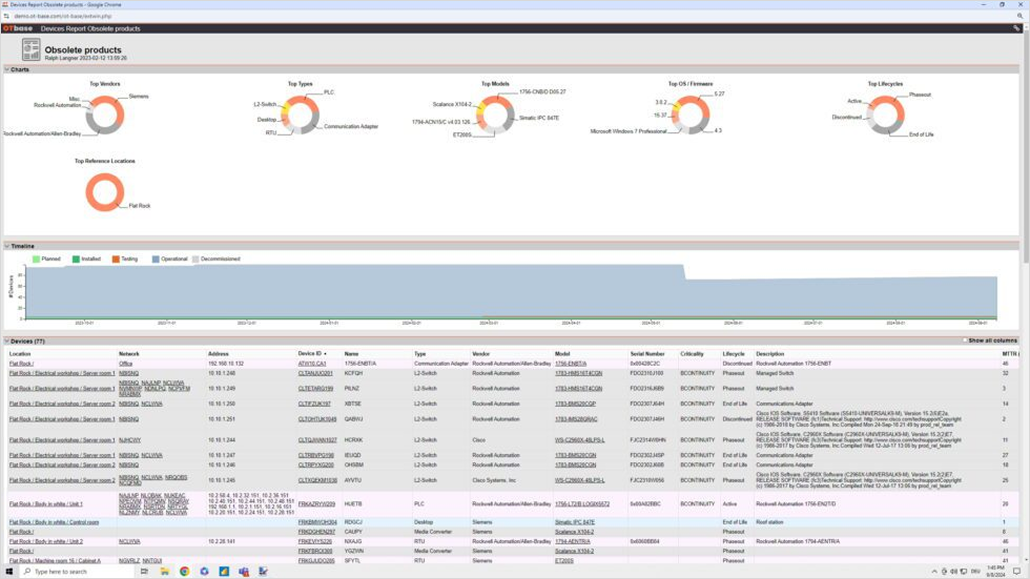
In operational technology (OT) environments—think industrial control systems, SCADA networks, and manufacturing floors—asset visibility is the foundation of security and reliability. Yet most organizations still rely on fragmented spreadsheets or…

Accurate OT Asset Discovery Is the Key to Real Cybersecurity
By Walt Boyes You can’t protect what you don’t know you have. OT Cybersecurity is directly linked to your asset inventory, as well as the control systems you are running.…

Why Context Is the Missing Link in OT Asset Management
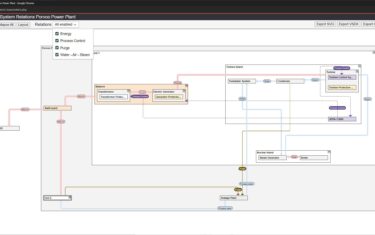
By Walt Boyes Now that you’ve torn out your hair, banged your head on your desk, and asked your boss to find somebody else to run OT asset management, he…