Effective OT Vulnerability and Exposure Management
Forget everything you know about OT vulnerability management: CVE “probabilities” and “likelihoods”, IT-style vulnerability “scans”, working from CISA or vendor documents to figure out if you are affected… None of that exists in OTbase.
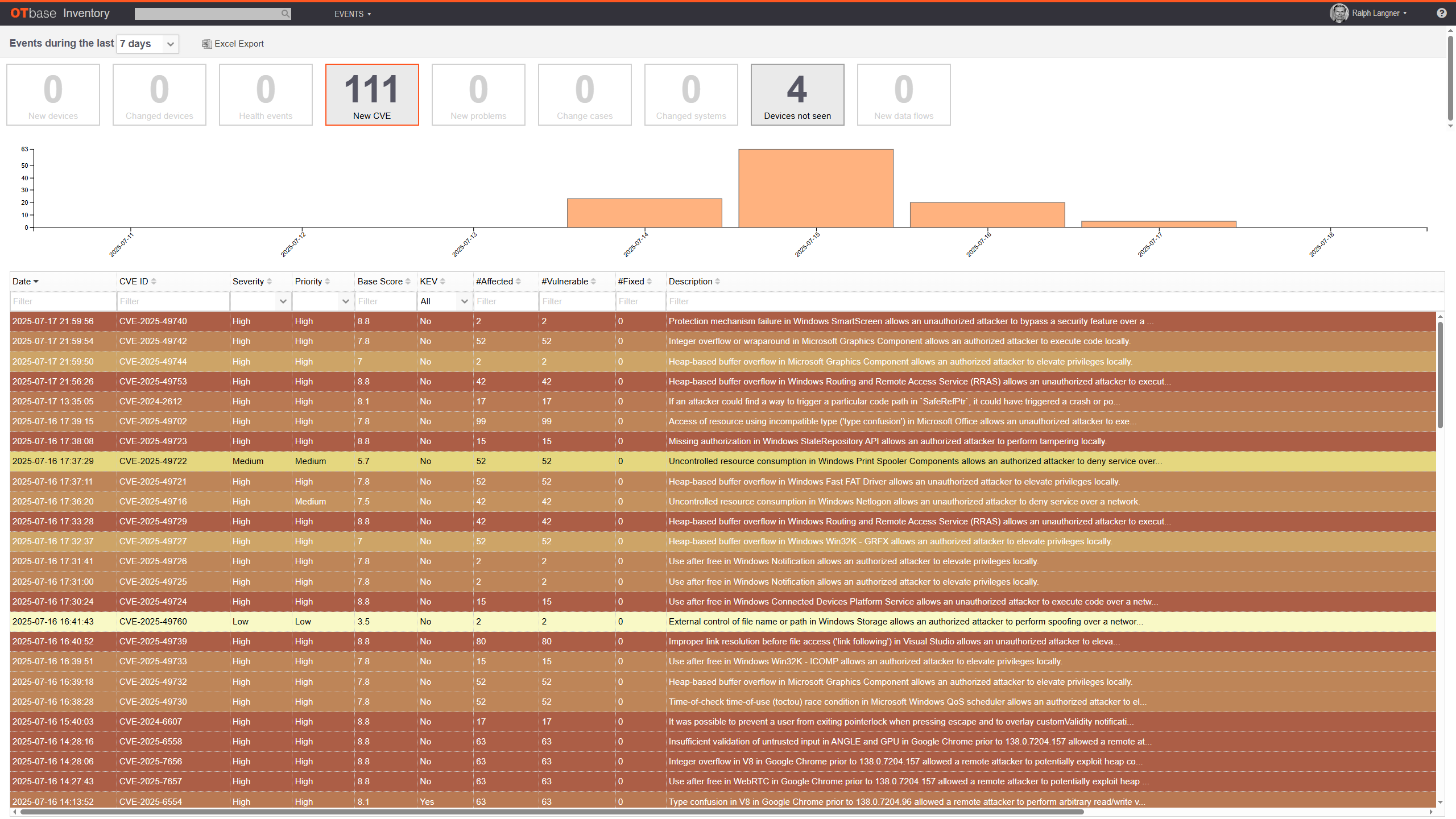
OTbase automatically matches CVEs against your installed base, without ever having to execute a vulnerability “scan”. Every 24 hours.
Meaningful
Attack Surface Reduction
Most asset owners approach vulnerability management in an anectodal fashion. CISA publishes a new report with nasty vulnerabilities, and management scrambles the team to figure out if it affects the company. A process that usually takes days, if not weeks. It will never lead to meaningful reductions of the attack surface.
Not with OTbase. It automatically exposes every single CVE that affects your installed base — without any “probabilities” and “likelihoods”.

Here’s how it’s done:
Detect vulnerabilities as they come in
OTbase automatically shows you which CVEs affect your installed base, updated every 24 hours. It also sends email notifications if desired. No CVE “probabilities”, no “CVE-EOL”, but all the details.
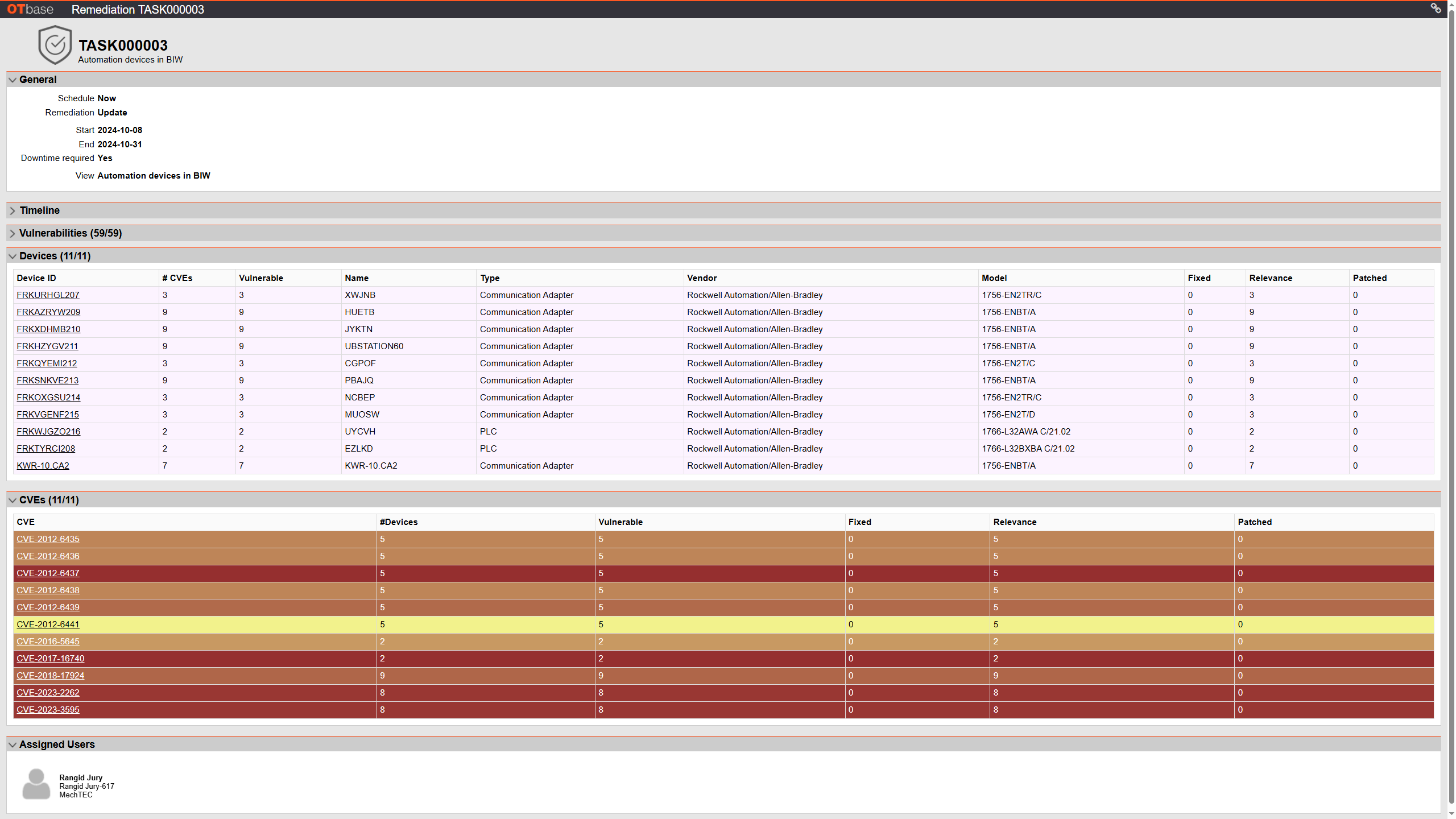
Prioritize vulnerabilities
The elaborate analytics in OTbase allow you to analyze which vulnerabilities must be mitigated with priority — based on factors like known exploits, attack vector, network exposure, and device criticality.
OT vulnerability management is one of the most misunderstood topics in OT security. Let’s change this.
The OT Vulnerability Management Handbook from OTbase outlines a performance-based approach shaped by more than twenty years of experience in OT security consulting in everything from automotive factories to nuclear power plants. Topics include:
- A known vulnerabilities primer
- Understanding the foundation of OT vulnerability management
- Furnishing a mitigation strategy
- Planning and execution
- And Monitoring and reporting progress
Fill out the form and download a copy of the handbook now.