OT Vulnerability Management that makes a difference
OT vulnerability management is a numbers game. In OT, you typically have to deal with hundreds of thousands of known vulnerabilities that affect your installed base — impossible to fix them all. OTbase helps you to understand what’s important and what’s not, and to make demonstrable progress.
Know which CVEs affect your installed base
All the CVEs that affect your installed base, in a table that you can slice and dice, and export to Excel. Sort the result set by CVSS base score, number of affected devices, or other criteria. Limit the scope to a particular site or class of networks, such as realtime or safety networks. Show only CVEs with known exploits.
See new vulnerabilities as they come in
The vulnerabilities dashboard in OT-BASE informs you about recent vulnerabilities that dropped in during the last 24 hours, last week, or last month. Also available as email notifications.
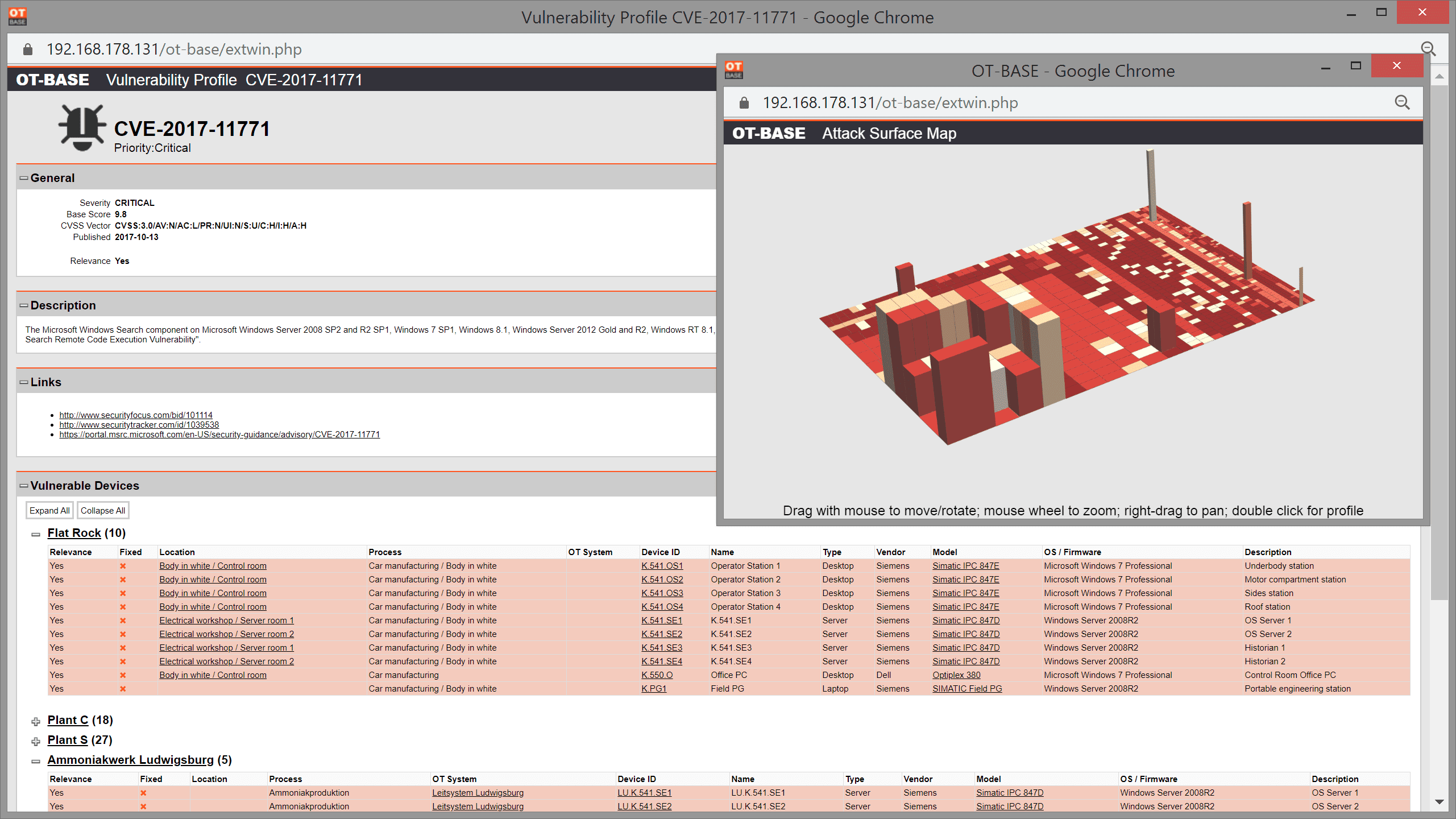
Check CVEs and patch status for individual systems
Check which vulnerabilities affect a particular device, and how regularly this device was patched. Limit the listing to CVEs with known exploits to highlight the really bad stuff.
Analyse the impact of individual CVEs on your installed base
See where you have systems that are impacted by a particular CVE by a click of the mouse. Compare criticality of CVEs using a 3D heatmap.
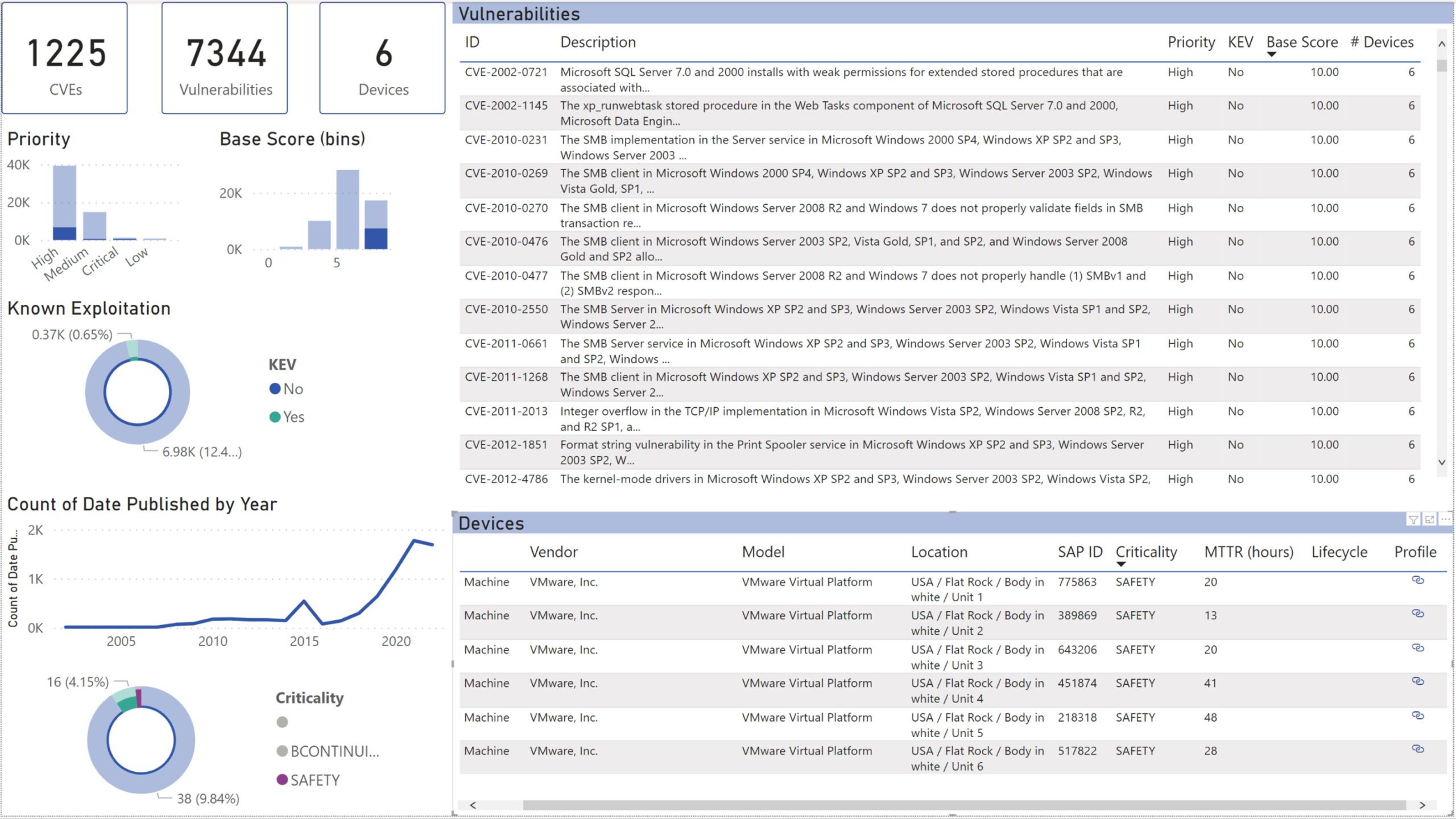
See the big picture in Power BI
Need a powerful dashboard to analyze and present your vulnerability analysis? Just use Power BI, pulling vulnerability information directly from OTbase.
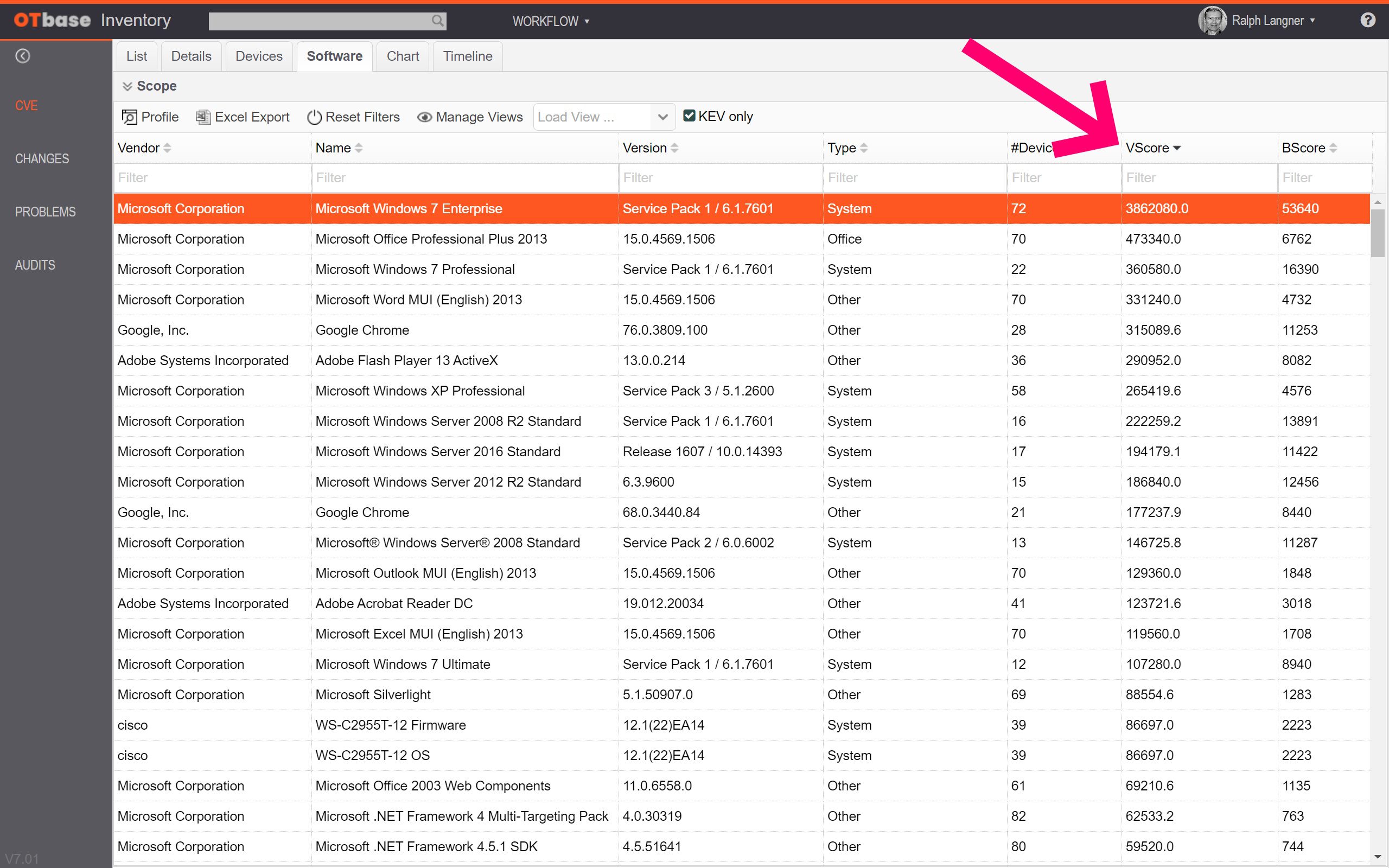
See which software contributes most to your cyber risk
Identify individual systems most at risk
Individual systems that carry extraordinary high risk levels may call for out-of-band mitigation activities. OTbase ranks all devices based on how much cyber risk they carry, based on cumulated CVSS base scores, device criticality, and network exposure. This way you can immediately see where invervention is called for right away.
Learn how OTbase helps you to build an efficient OT vulnerability management process with these videos

Enterprise-grade OT asset management software