OT Security Blog Articles
Insights on Resilience, Vulnerability Management, and More
Why Ethernet/IP changes the OT asset discovery game
Ethernet/IP has become the predominant industrial network protocol, which is good news for everybody attempting to implement comprehensive asset management for OT. If you are using Ethernet/IP, it's fair to say that you're in the best position to solve the asset...
Why you need an OT/ICS software inventory, and how to build one
In OT security circles we are recently witnessing a myopic fixation on one single security control: Network anomaly detection (NAD). As any cyber security practitioner can tell you, NAD is not a cure for all diseases, and you are going need more than a truckload of...
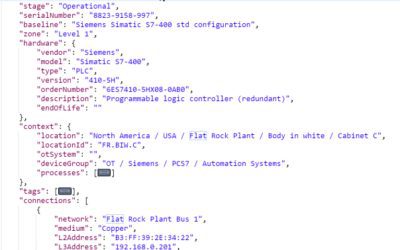
What is OT/ICS configuration management, and how does it benefit engineers, admins, and auditors?
OT configuration management is the process of assuring consistency of OT system design with requirements. It helps you to gradually arrive at more robust network architectures, standardized software configurations, better maintainability, and higher security posture....
When will we see another Stuxnet & Nitro Zeus attack against Iran?
Eight years after we had uncovered that Stuxnet was a targeted cyber-physical attack against the Iranian nuclear program, both the United States and Israel find themselves threatened by the prospect of an Iranian breakout towards nuclear weapons production. This...
Importing OT/ICS Asset Data into your Enterprise Applications
Suppose you already have a great OT asset management system. It automatically discovers the identity and configuration of your PLCs, RTUs, network switches, operator stations and so forth. Your engineers use this system as their central hub for documenting the...
Understanding OT/ICS Asset Discovery: Passive Scanning vs. Selective Probing
For businesses large and small, digital operations technology has become a key driver of efficient production. But honestly, do you still exercise full control over your OT assets? If you are like most asset owners, you probably don't know exactly how many PLCs, RTUs,...
Misjudging OT security risk, part 2: Comparing cost/benefit
In a preceding blog article we discussed the logical flaw in network anomaly detection marketing collateral: Vendors emphatically advocate "passive scanning" with the argument that "active scanning" would be too dangerous, yet focus on completely different risks...
Misjudging OT security risk: The case of “active” vs. “passive” scanning
If you have followed the marketing buzz in the OT security software space, you cannot have missed the hype around "passive network scanning", which is a hallmark of network anomaly detection products. Interestingly, this buzz expects you to ignore the following...
Die fünf besten Schutzmaßnahmen gegen Cyber-Angriffe und Schadsoftware
Wer die Medien verfolgt, weiß: Ausgefeilte und umfangreiche Cyber-Angriffskampagnen nehmen zu. Das führt gemeinhin zu zwei unterschiedlichen Reaktionen. Einige Beobachter verfallen in Fatalismus, da gegen staatliche Angreifer aus Russland, China usw. wohl ohnehin kein...