Get a real OT asset inventory, without hardware sensors
OTbase is a purpose-built OT asset inventory tool that probes deep into your process networks, down to level zero where sensors and actuators live. Developed by the team that cracked Stuxnet, and used by some of the largest enterprises in Manufacturing and Oil & Gas for their global operations.
Here’s how it’s done:
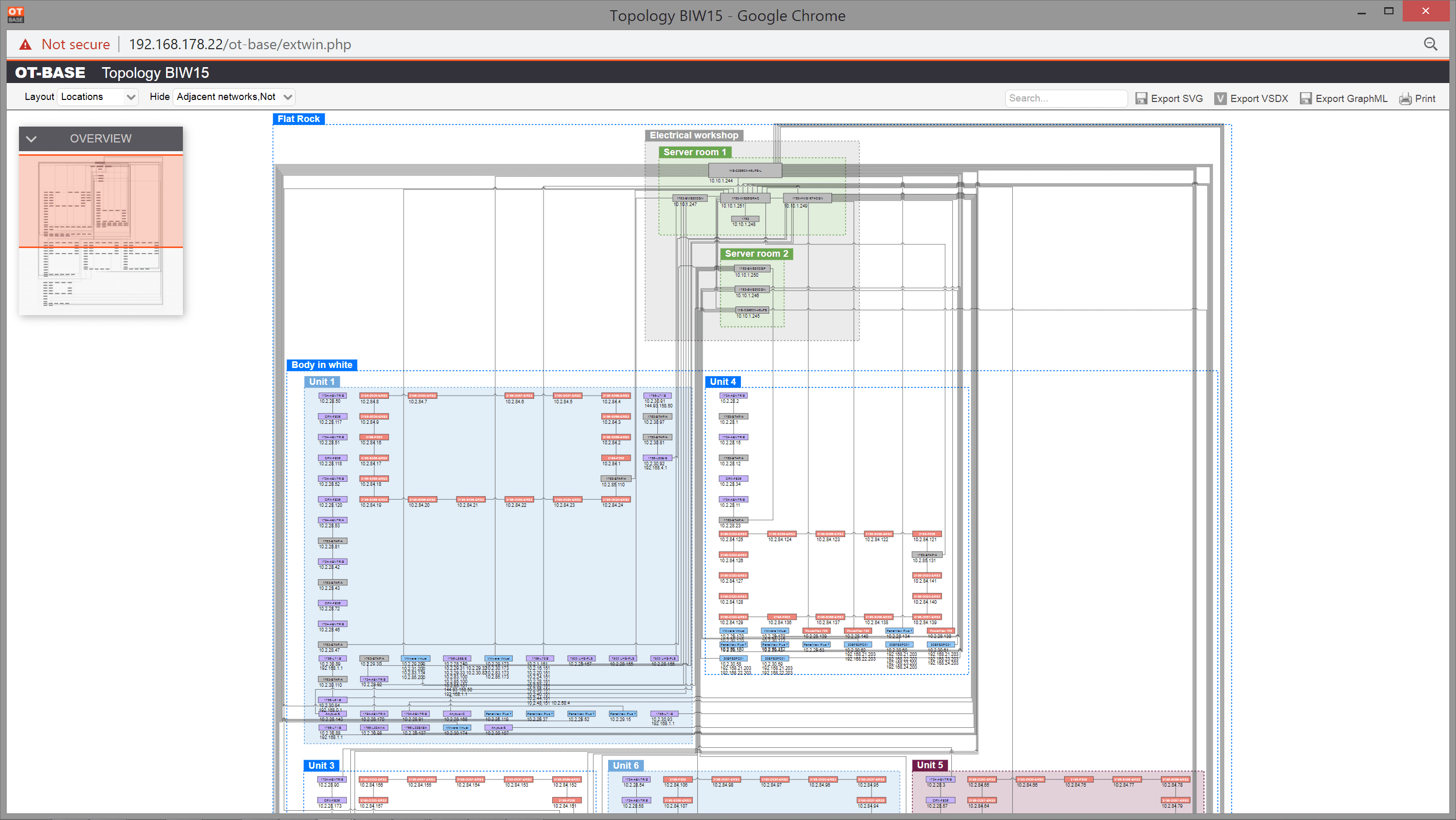
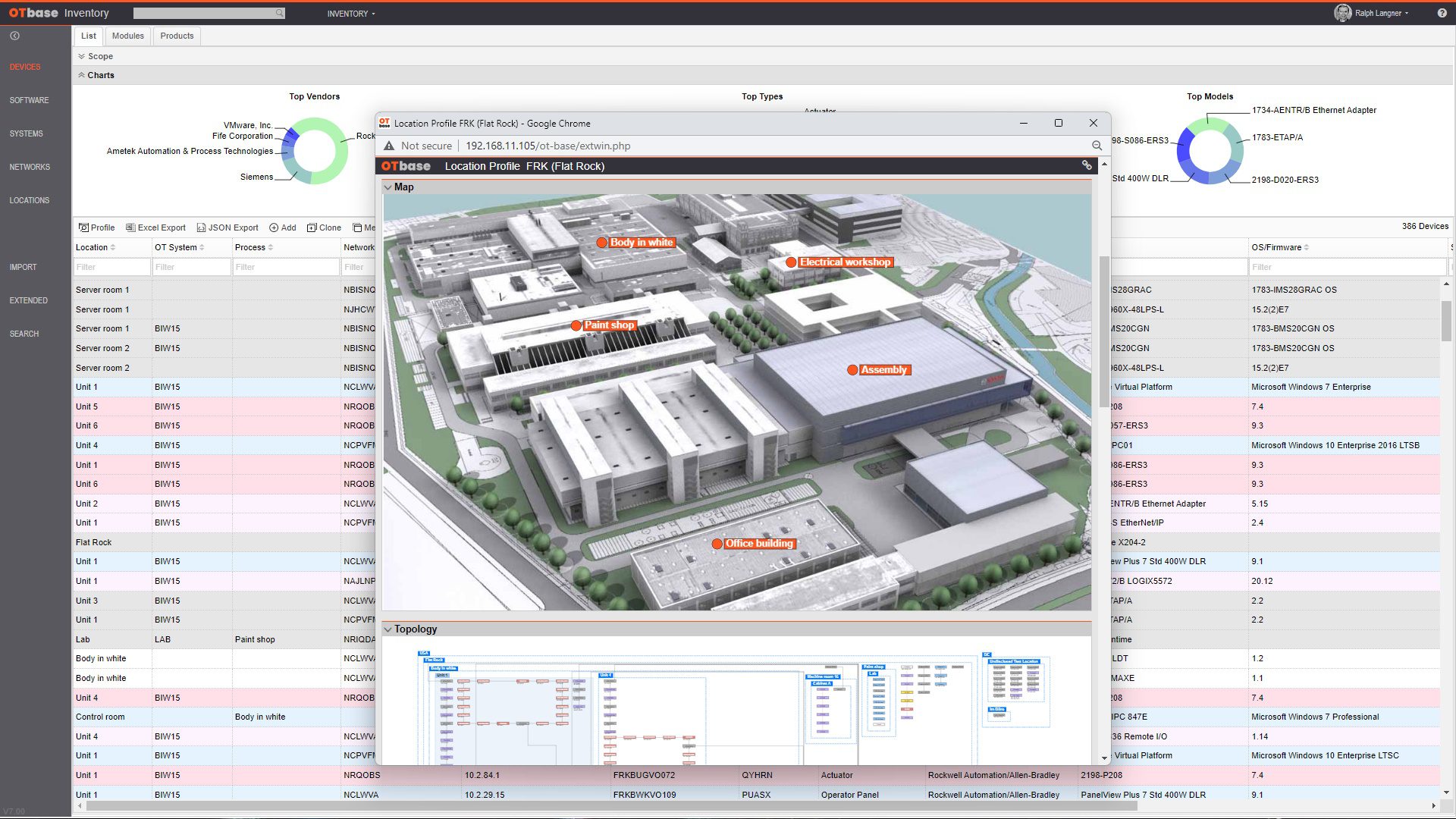
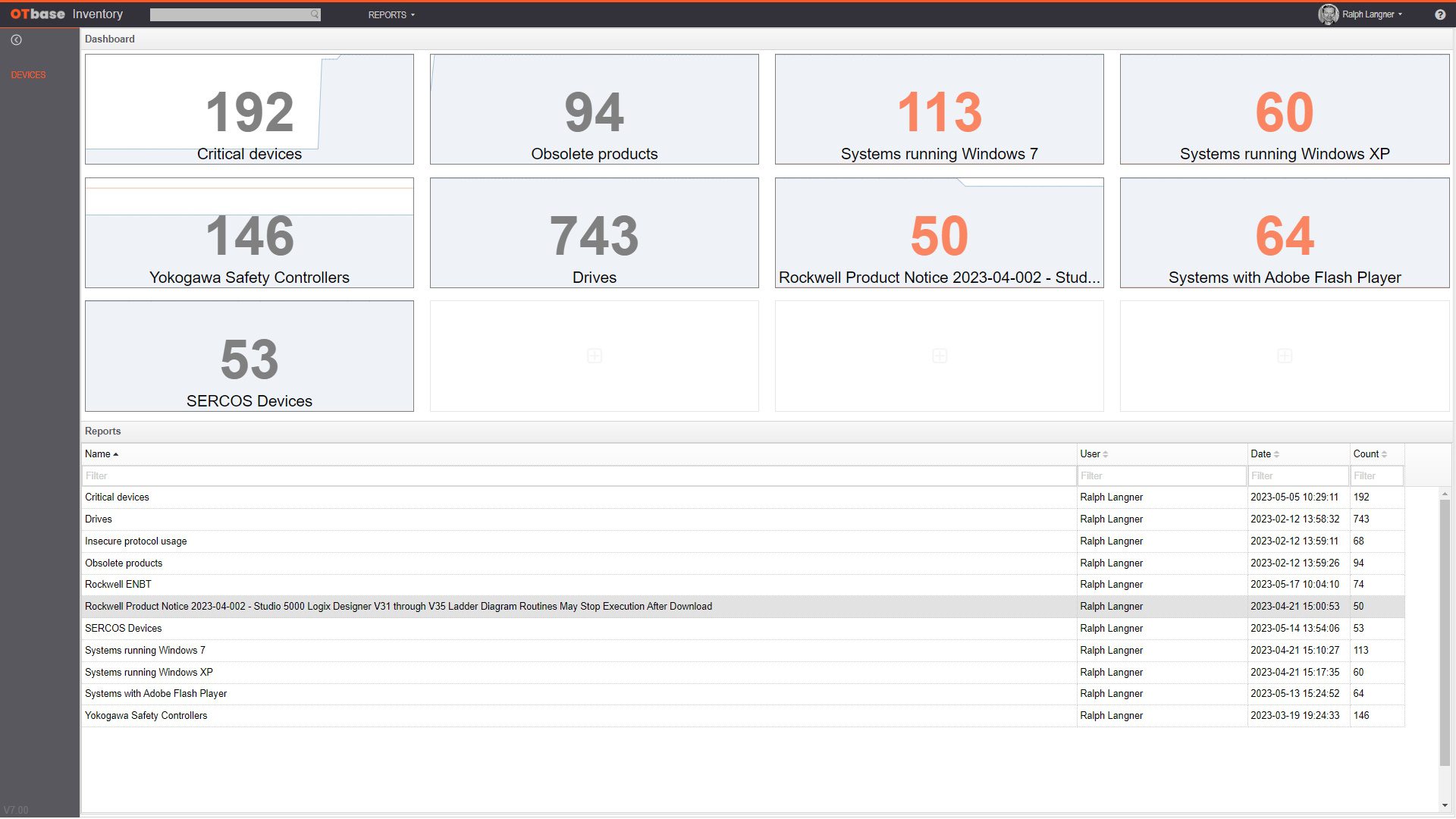
1. Create a contextualized, evergreen OT asset inventory
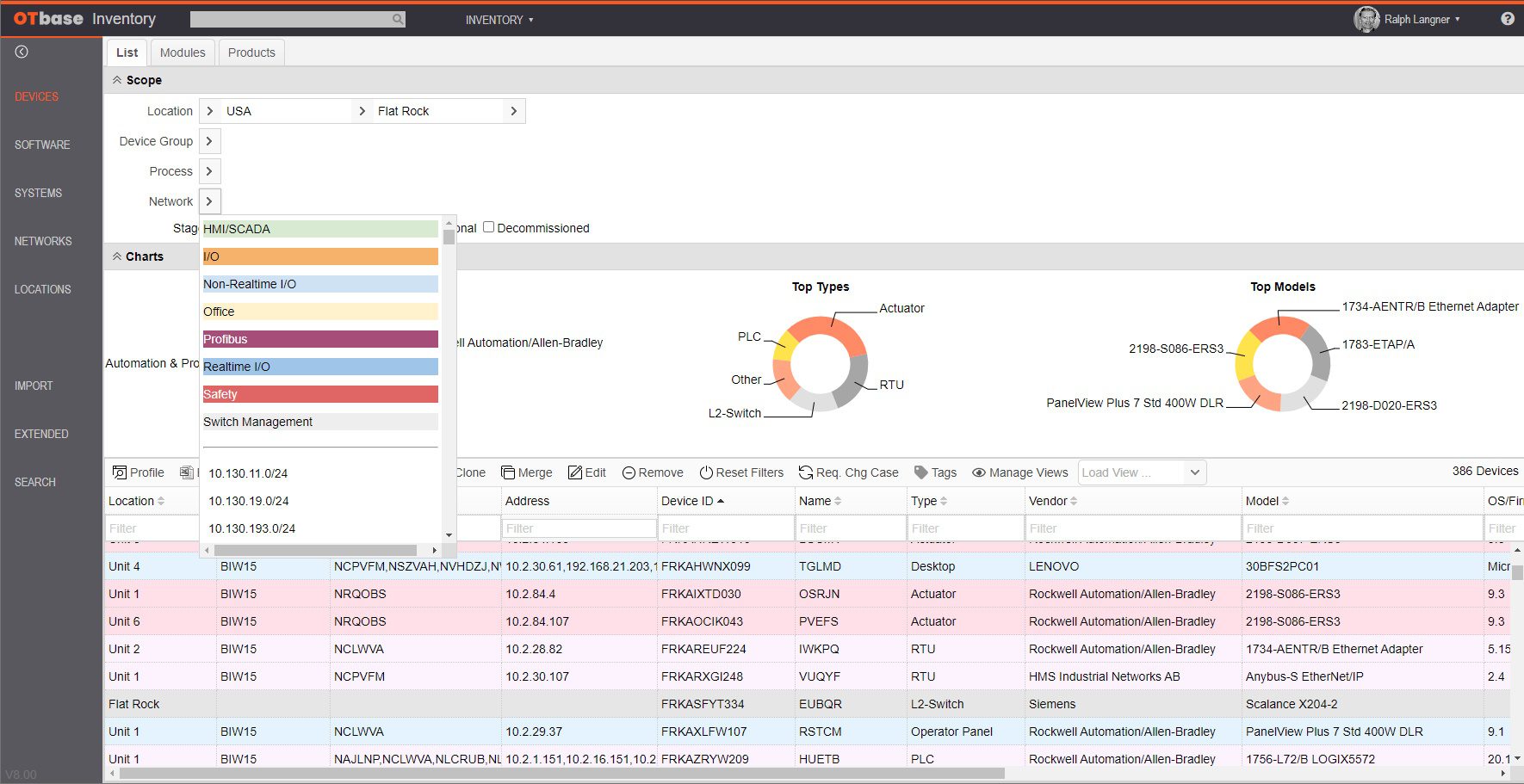
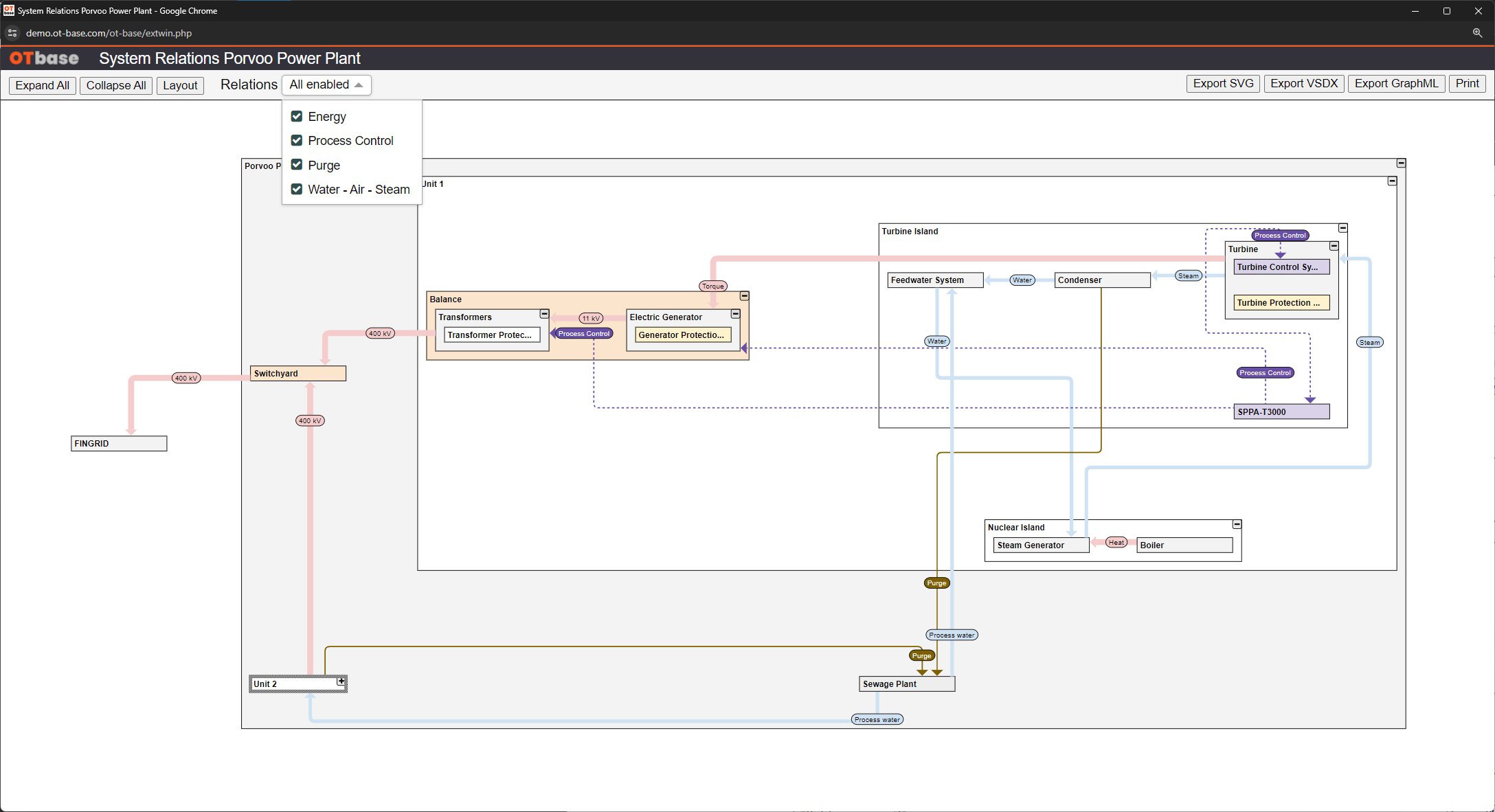
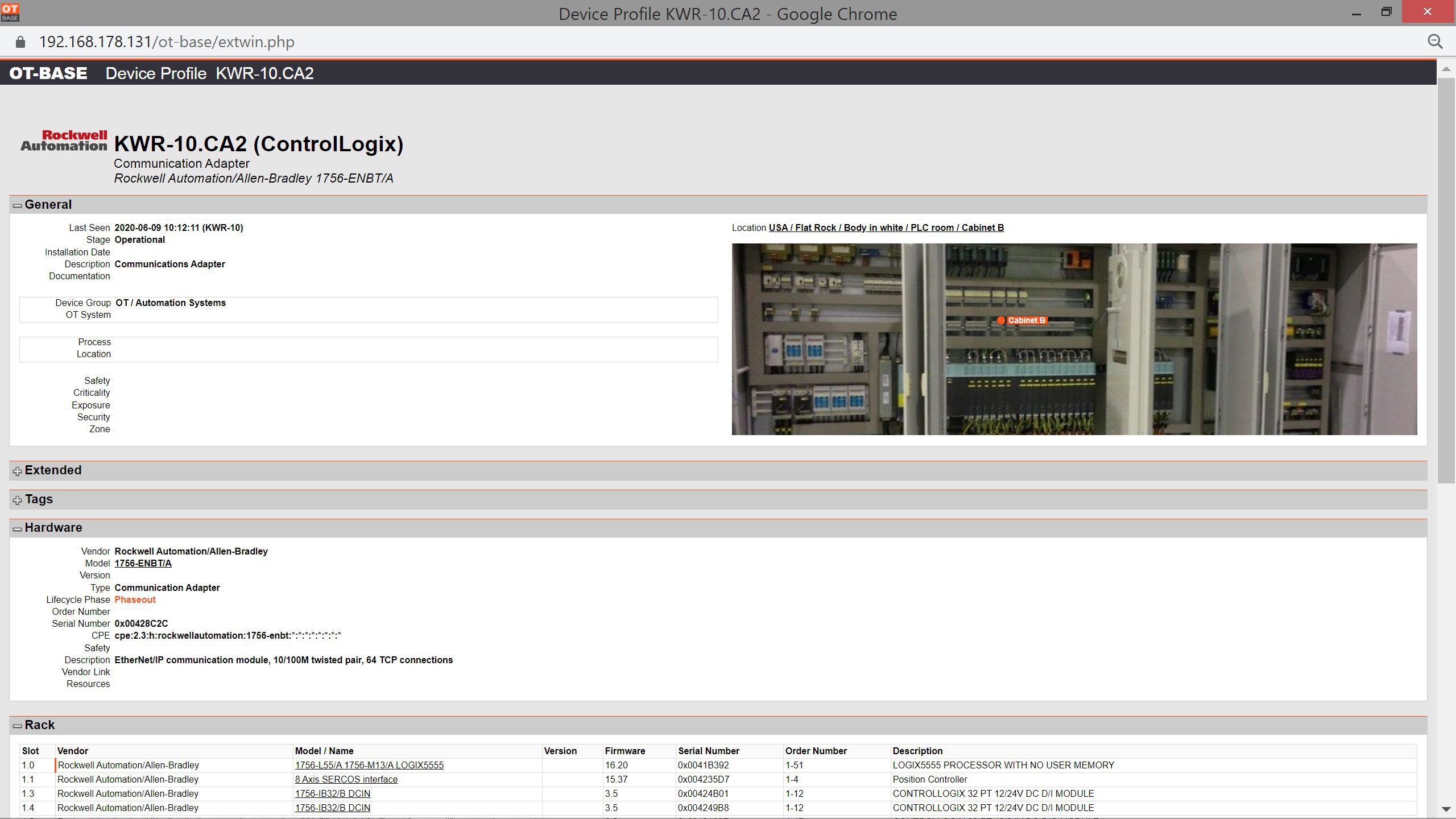
OTbase automatically inventories your OT devices, networks, and software. You don’t need to deploy hardware sensors. Daily updates ensure that you don’t miss configuration changes and new devices on the network. You can easily add context such as geolocation, ISA 95 system hierarchy, custom fields, network groups, and more.
Learn more >
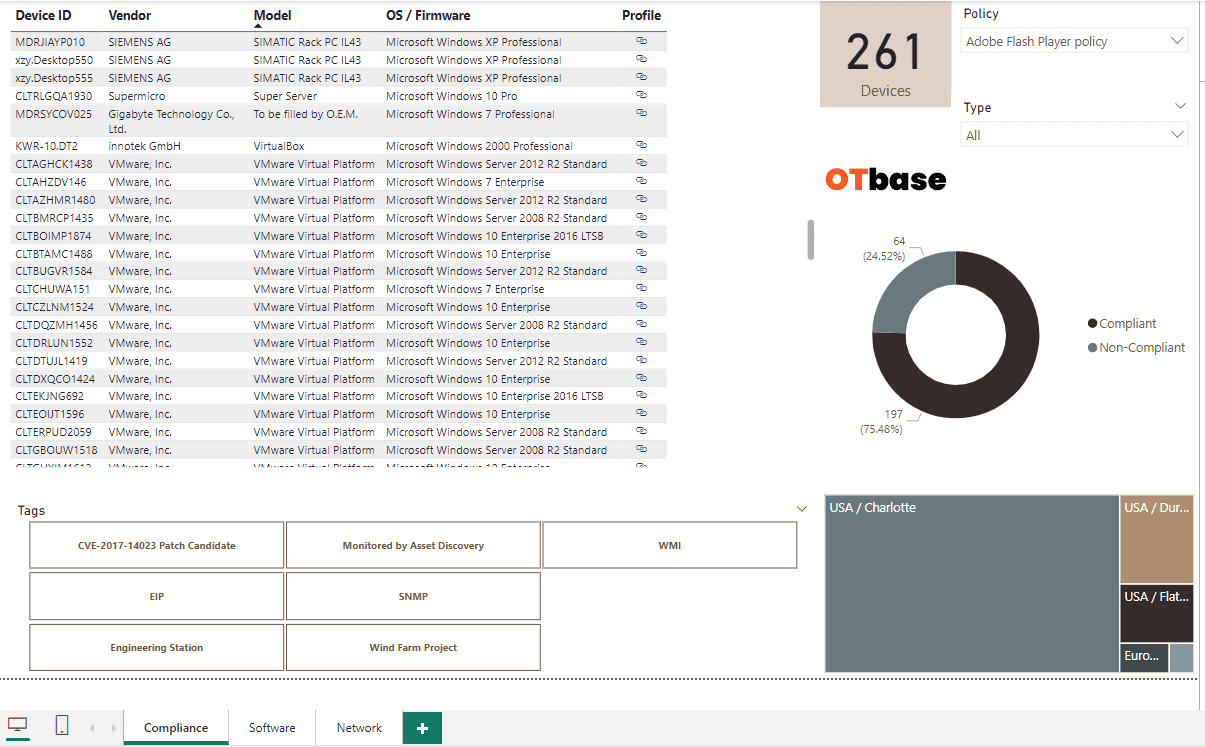
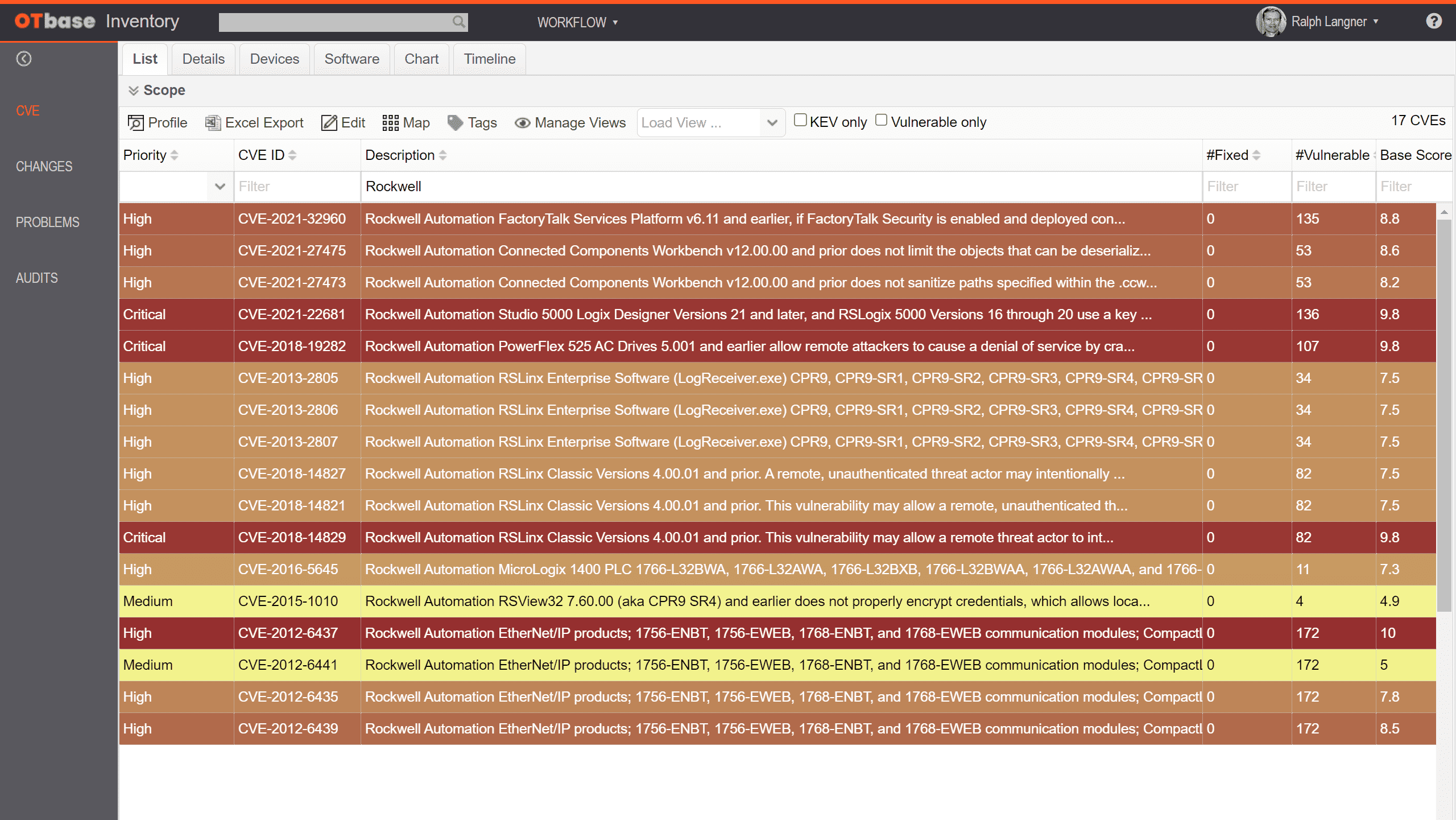
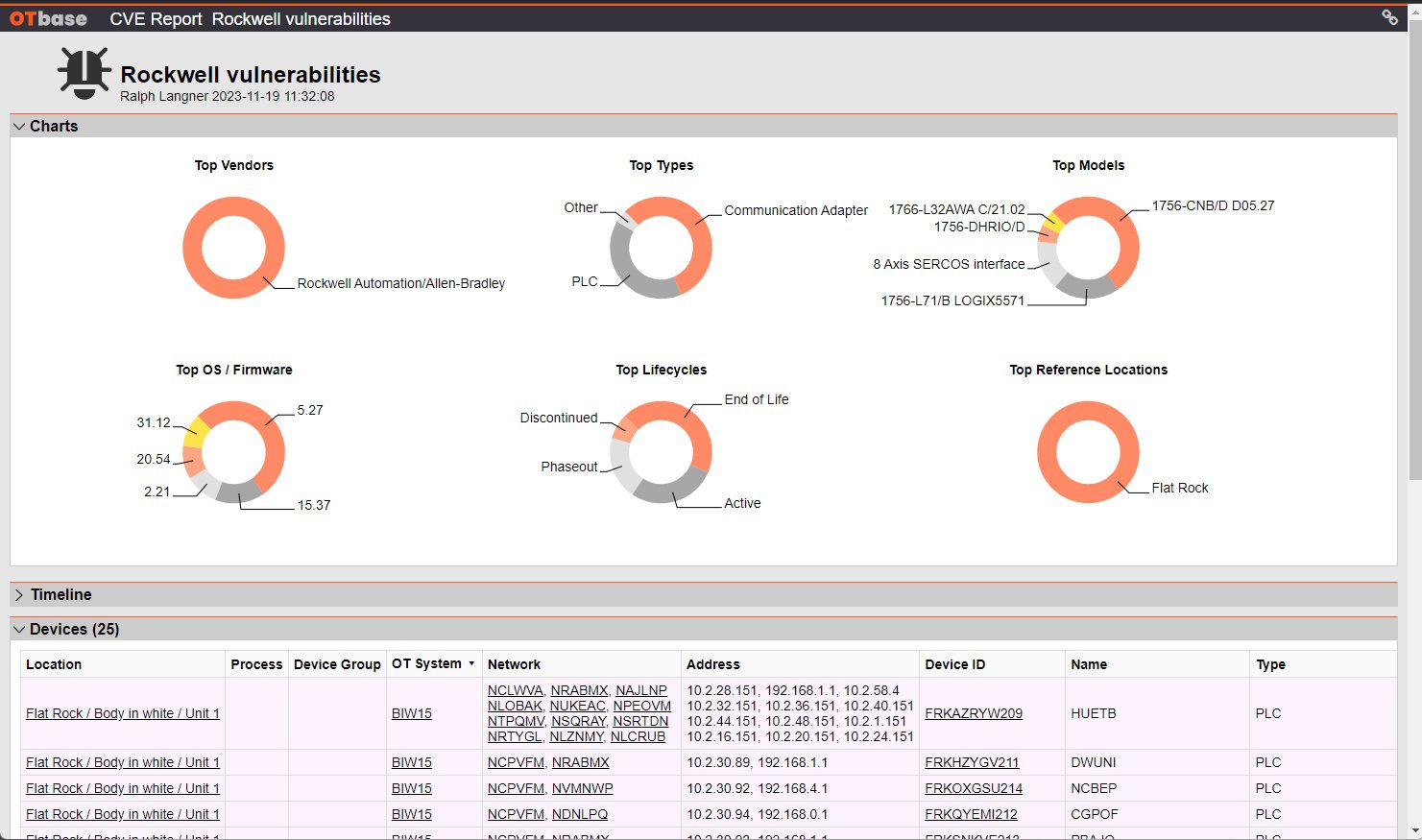
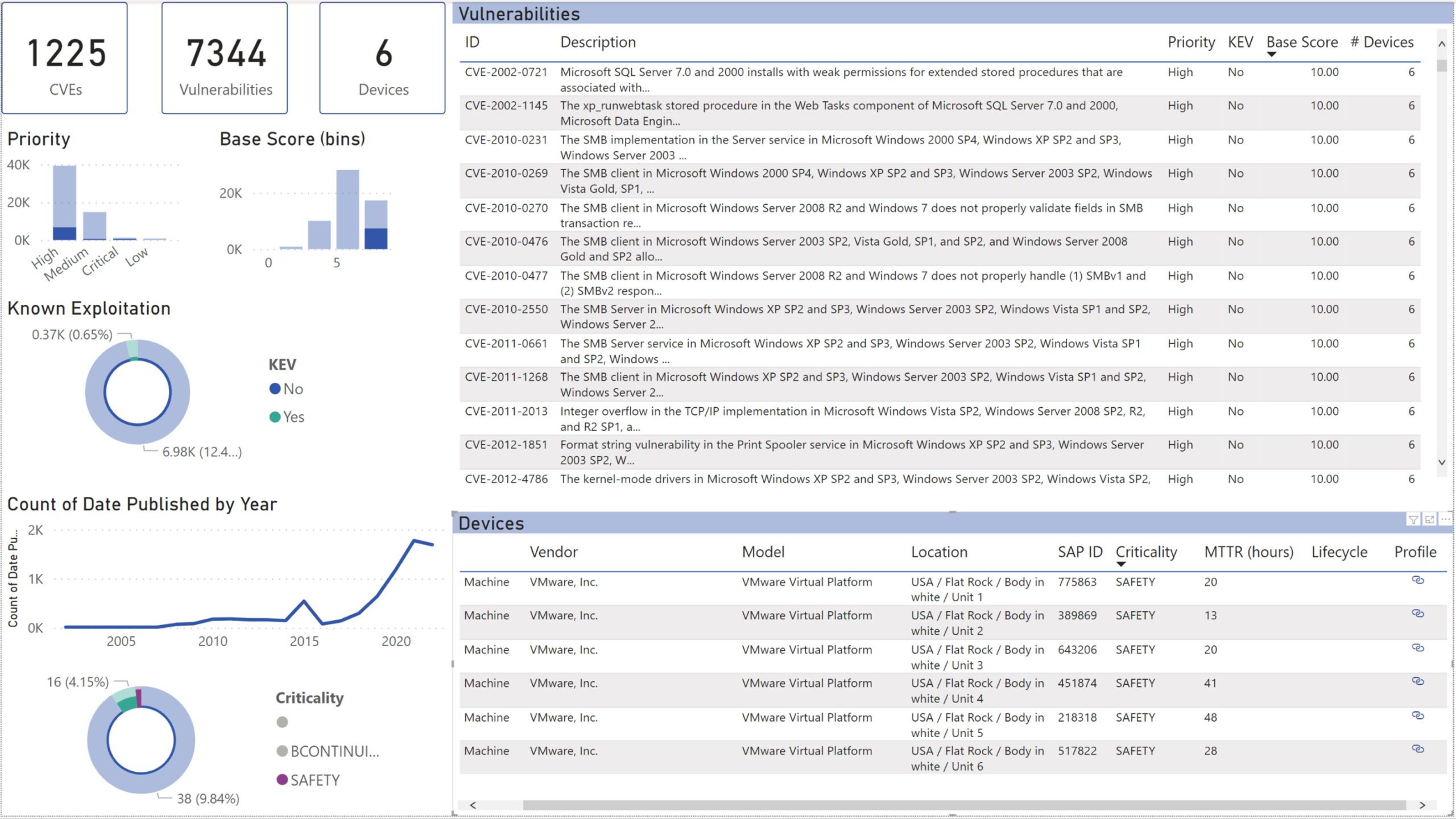
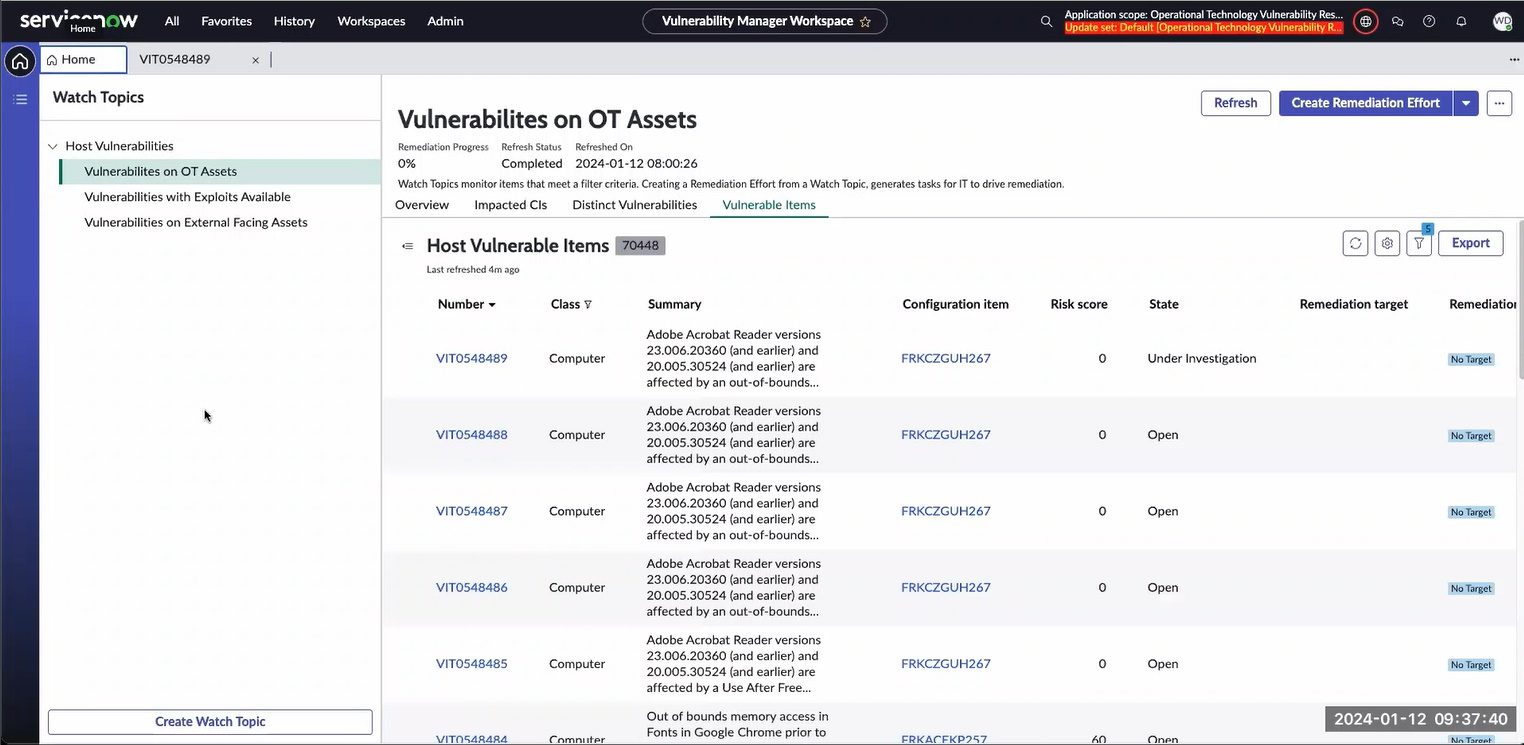
2. Implement performance-based OT vulnerability management
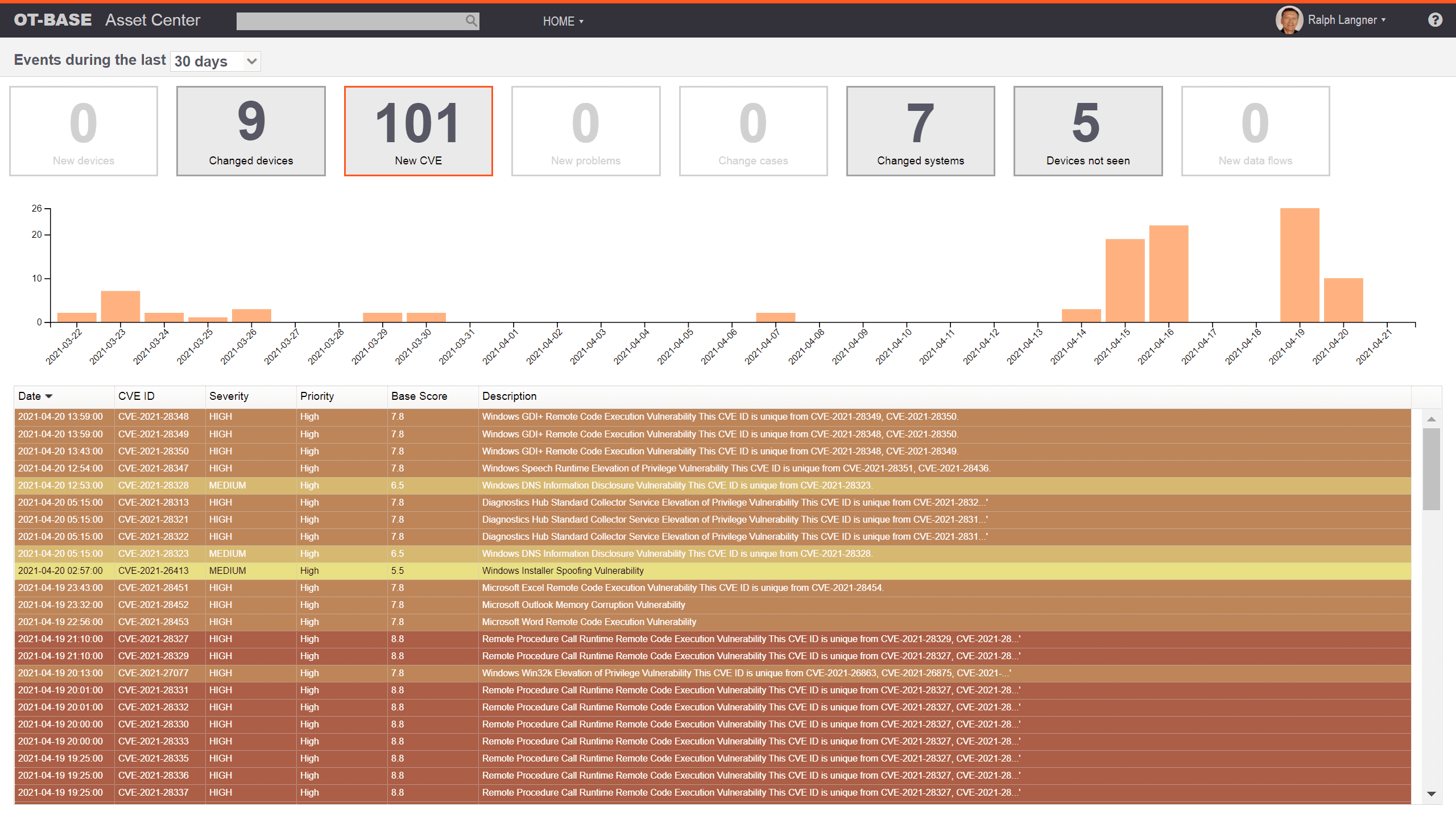
See all CVEs that affect your installed base without ever executing a “vulnerability scan”, or having to deal with vulnerability “probabilities”. OTbase does all the heavy lifting behind the scenes. Use prioritization to build an effective OT vulnerability management strategy, to arrive at the results that management wants to see.
Learn more >
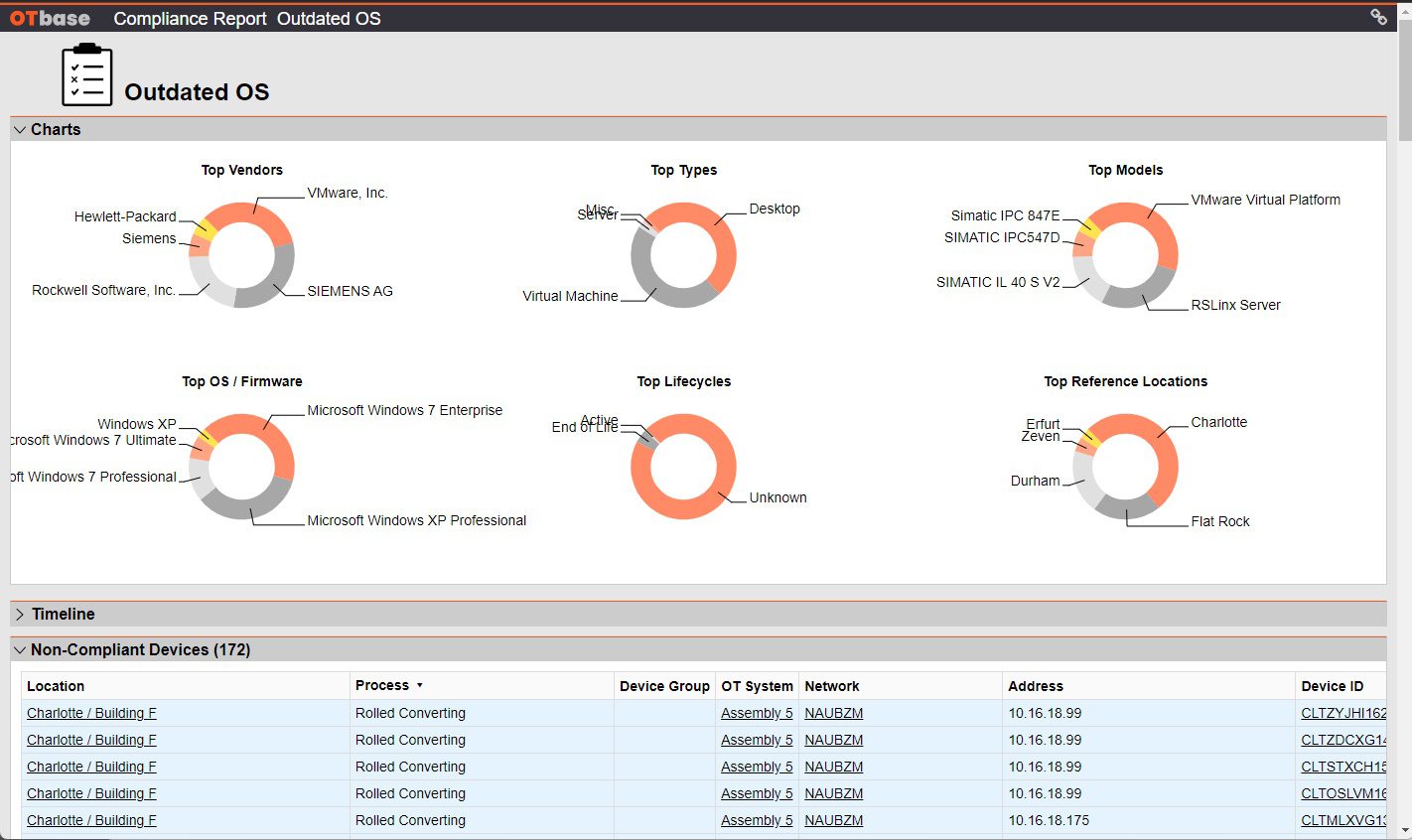
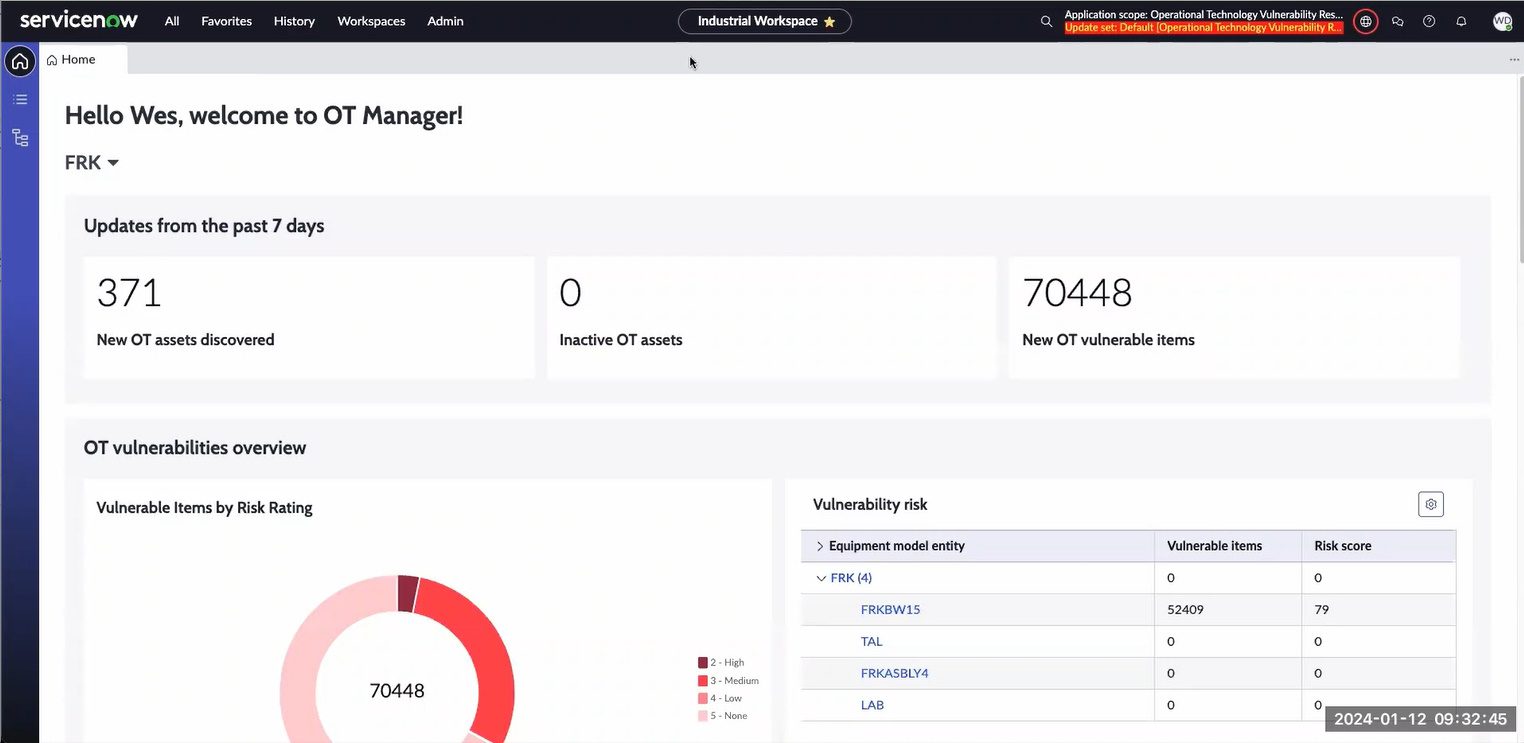
3. Create awesome reports that make management happy
Management wants to see key performance indicators and trends. OTbase gives you all the reports you need to show you are on top of things. Choose between self-updatinig native reports, or use Power BI to create CISO dashboards in a couple of hours.
Learn more >
Once you’ve seen it
you will never want to go back.
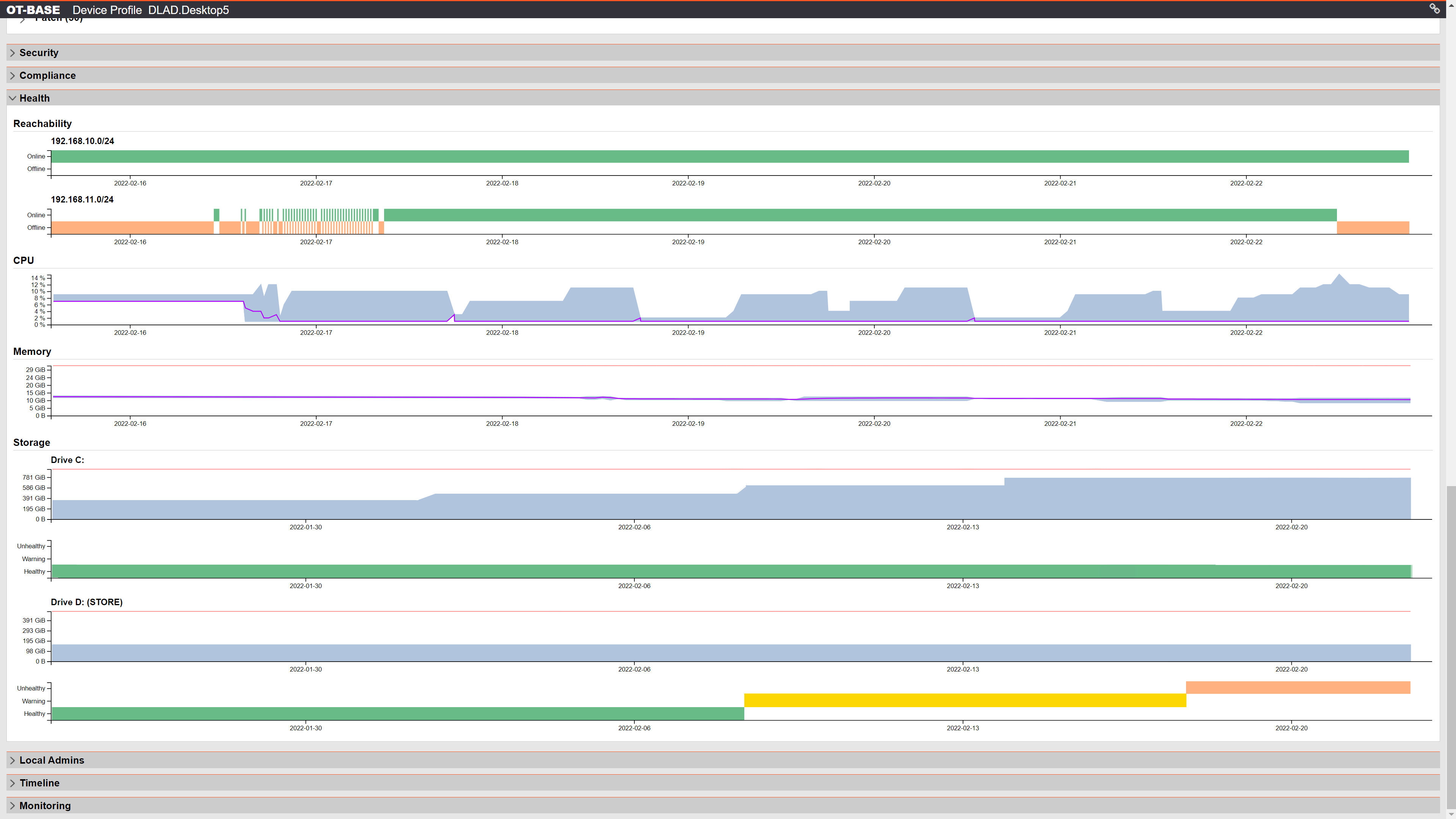
OTbase provides full transparency on all aspects of your OT networks, from minute configuration details to high level KPIs in a CISO dashboard. OTbase enables cyber security experts, control engineers, maintenance experts, plant planners, process engineers, and SOC analysts to get the information they need in an instant.
Feeling like you are outgrowing your OT Threat Detection solution?