What is OT, and what is an asset?
OT is an acronym for operations technology, which basically means digital technology used for industrial control in a broad sense. All of the following are achieved with operations technology:
- basic process control,
- control of ambient process conditions (HVAC, clean air),
- safeguarding of workers and the environment,
- protection of industrial machinery from exceeding design limits,
- assurance of product quality.
Operations technology usually has a physical and a realtime component, such as controlling the operation of an automated assembly line or chemical reactor. Sometimes the acronym ICS (industrial control systems) is used as a synonym for this subject, but OT has become more popular as in today’s industrial environments, many critical digital components such as network switches don’t qualify as control systems in the strict sense. In this article, we will only use OT and trust that the reader understands that ICS is covered as well.
An OT asset is a digital device that is part of an OT infrastructure. Devices can either be physical or virtualized. One can argue that there are other types of OT assets besides digital devices, such as software assets. From a theoretical perspective, that argument has its merits. From a practical perspective, experience has shown that it is most efficient to identify OT assets with devices, while software, networks etc. are conceived as their configuration attributes. In other words: We didn’t forget about the software, it’s just not listed as assets in their own right.
An OT asset almost never works in isolation but in concert with other OT assets with which they form an OT system. OT systems vary in complexity from a handful of assets to over thousand. Different from IT, malfunction of a single part (asset) of an OT system often affects overall system behavior. As an example, when a single PLC in a production line fails, it affects the whole production line (and maybe even other processes in the supply chain). When a single workstation in an IT environment fails, the effect is often local.
Asset inventories and the “single source of truth”
In order to manage anything, it is necessary to have a practically useful representation of the thing that is to be managed. In the case of asset management, this representation is an asset inventory — a system of record that lists OT assets along with their major characteristics such as make and model, location, and their hardware and software configuration.
Sometimes an asset inventory is also called the “single source of truth”, as it is thought of as the authoritative reference on how OT assets are, and should be, configured. While parts of this information may also be present in other software applications (such as a service management platform, a SIEM product, an ERP system), having only a single authoritative source comes with an advantage. If there is ever doubt about the validity of data, reverting to the single source of truth resolves the issue. And in order to assure data validity, the organisation only needs to make sure that one system (the asset management system) has accurate information, which is not particularly difficult through automatic asset discovery.
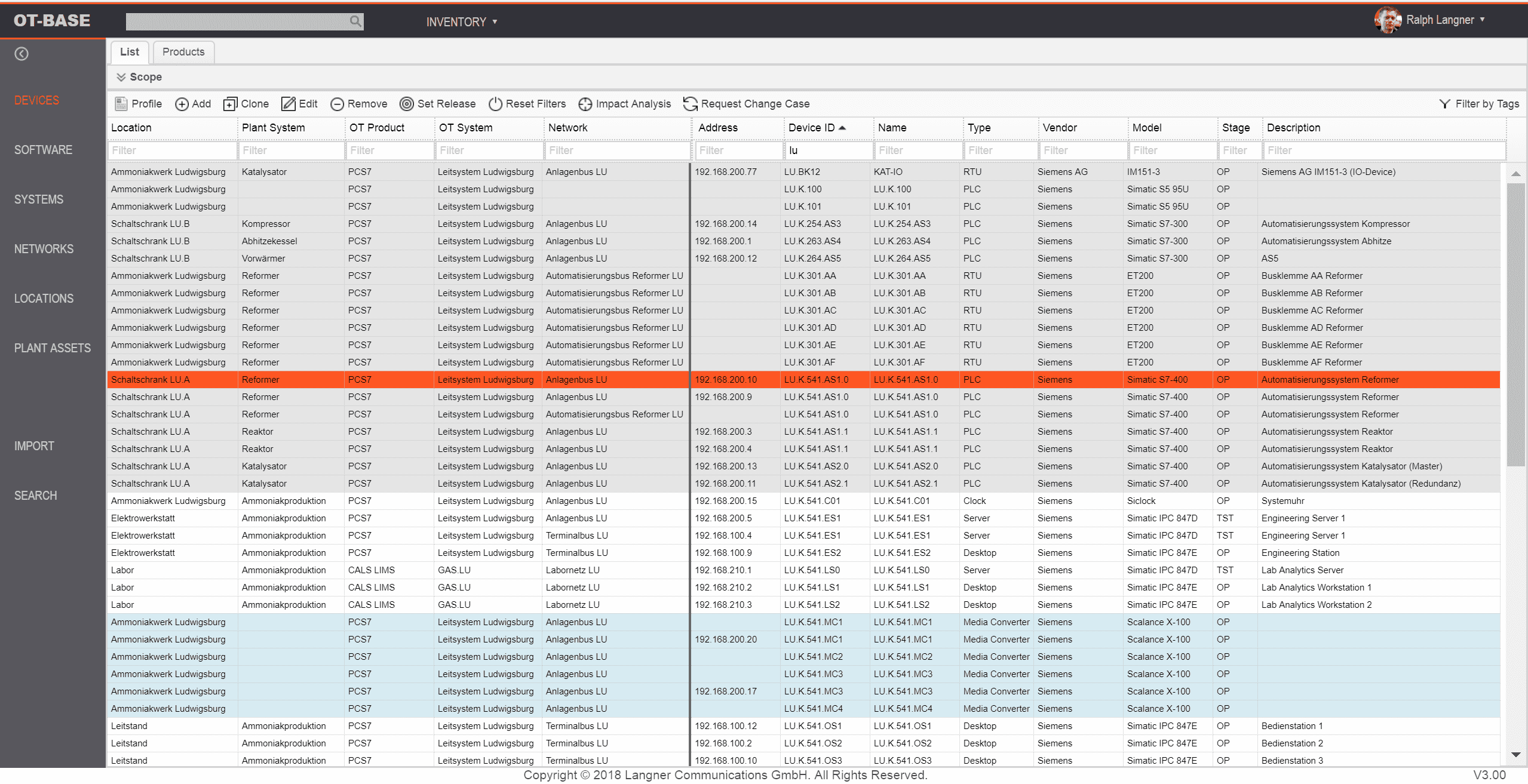
Asset discovery: Active vs. passive
Even today, a majority of organizations attempt to maintain OT asset inventories using Microsoft Excel. Excel is a great tool many of things, but OT asset management is not among them. Abusing Excel for creating an asset inventory implies manual data collection (“discovery”) — by an already overworked engineering and maintenance department. The reality is that no organization has the resources to manually gather configuration data from reasonably sized OT environments; a task that needs to be repeated periodically in order to keep track of configuration changes.
Technically, automatic discovery of OT assets can be accomplished by two different approaches: Active and passive. The passive approach, also called “passive sniffing”, analyzes network traffic in a particular subnet and infers device characteristics (such as make and model) from the packets flying by. The active approach, also called “active probing”, sends out targeted probes to devices on the network. It asks OT devices using legitimate industrial protocols about configuration details such as make and model, installed firmware, and so on.
“Passive sniffing” used to be the method of choice for asset discovery until buyers found out the hard way that in terms of economics, it doesn’t scale. Passive relies on a network appliance in each subnet for digesting processing realtime network traffic from a switch’s SPAN port. That may not sound particuarly alarming when one is operating less than ten networks, but it becomes an outright road block when talking about hundreds of networks.
A similar situation exists for small, dispersed networks as they are typical for water utilities, renewable energy power plants, and oil rigs: If the networks that need to be discovered are in the middle of nowhere and only consist of a handful of devices, sending out an engineer to install a network monitoring appliance is overkill. Especially when those same networks can be monitored from afar by active probing.
Adding context and meaning through metadata
Automatic asset discovery yields a wealth of information about individual OT assets and their configuration. This data becomes ten times more useful when enhanced with metadata that basically reflects contextual asset attributes. Metadata is “data about data”. Consider the following items:
- Physical location of a particular OT asset (such as site, building, floor, room, cabinet).
- A brief description what an OT asset does; for example: “Vibration monitoring server”.
- Association of an OT asset with an OT system, such as a particular production line, distributed control system etc.
- Network names and network types as used by engineering and maintenance. Imagine the only thing you would know about a network was its IP address 192.168.0.0/24. Unfortunately, there are dozens of networks in your company with that same address. Using a symbolic name such as “Packaging line 3, I/O network” will make network data much more useful.
- Asset criticality. Not all assets are equal when it comes to the effects of a potential malfunction. This is something that engineers usually are aware of. Recording criticality data in the asset inventory will go a long way for certain use cases such as vulnerability management.
Imagine an asset inventory that only had IP addresses recorded to characterize assets, and another one that also listed the above mentioned metadata. Both inventories refer to the same assets, but the difference in utility is striking. And it’s even more than utility; sometimes it’s a bare necessity. Consider, for example, that duplicate IP addresses are commonplace in OT environments. An IP address such as “192.168.0.5” may be in use multiple times. The only resort is the capability to distinguish between the various assets that use this address — by means of metadata such as location.
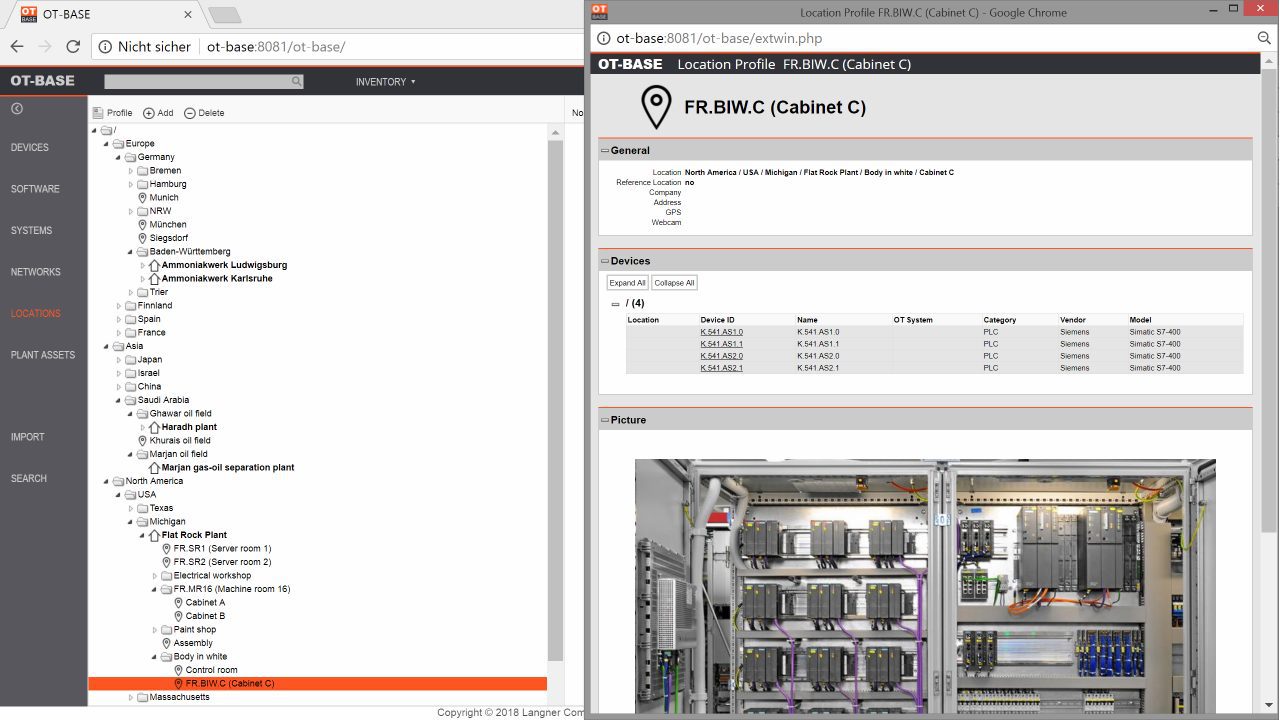
Metadata glues asset information to uses cases. Technical attributes on their own provide little value when they only exist in a vacuum, rather than being tied to environments of real-world users.
The “management” part of asset management: Use cases and workflows
OT asset management is the consistent determination that OT assets are configured to specification. The “consistent” part in this definition alludes to the idea that an organization wants to use and enforce standardized configurations across OT assets, rather than having engineers configure those assets individually, according to spontaneous needs. It also implies that conformance or non-conformance can be established throughout the board, without a need for walk-down verification.
An asset management system is a software product with an automatically maintained asset inventory at its core, and workflow automation for major use cases such as the following:
Change management: The OT asset management system is the foundation for a consistent change management workflow. It helps to plan, execute, and verify configuration changes in a structured and efficient manner. When planning, designing, procuring, testing, and commissioning new plant components or production lines — and hence, new OT systems –, it is important to assure that the new build complies with corporate standards and cyber security requirements well before commissioning time.
Vulnerability management: There’s no way to get a realistic idea of the cyber vulnerabilities in an OT environment without an OT asset management system — because there are just too much of them. (Why too much? Because OT environments are notoriously out of patch.) The asset management system shows which known security vulnerabilities apply to the installed base, and how bad they are. In order to do this, the asset management system references hardware and software product data, device criticality data, and device network exposure. Properly visualized, this data provides clear guidelines for risk triage and patch management.
Obsolescence management: OT installations have a much longer lifetime than IT. This can result in risk, as mission-critical devices may no longer be supported by the vendor when they need to be serviced or replaced. This problem affects both software and hardware. The asset management system can tell users in advance when critical products get discontinued, reach end of life, or end of support. This allows for planning mitigation in time.
Disaster recovery: When OT systems fail, it is not a good time to start figuring out how functionality can be restored. Failure and malfunction can have costly side effects such as loss of production and downtime. The well-prepared organization has created contingency plans in order to cope with such situations. However the question remains how quickly such plans can be accessed in the event of an emergency. The asset management system answers that question rather quickly: Having contingency plans for each device accessible within a mouse click is very convenient.

OT asset management and the NIST Cyber Security Framework
Having discussed vulnerability management already, there are other use cases under the umbrella of OT security that rely on asset management. In order to highlight the role of asset management for OT security overall, here’s a brief review how asset management is a foundational requirement for various areas of the NIST Cyber Security Framework:
Identify: Identification is a logical category for asset management, and the discipline is, no surpsise, explicitly listed as its first item. The basic idea here is that you cannot protect what you don’t know. One could go further and make the point that governance and risk assessments are practically impossible without reference to an accurate and complete asset inventory.
Protect: The OT asset management system tells you about the presence and efficiency of major technical security controls such as security patches and firewall rules. It also allows for determination where such controls might be missing, or malfunctioning. As an example, the asset management system knows about antivirus products being out of date or disabled.
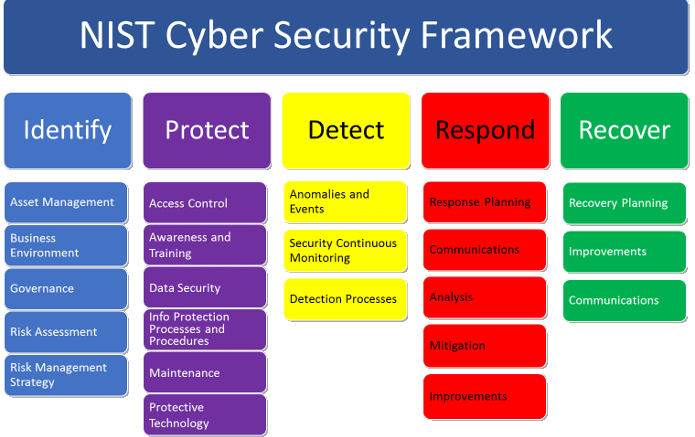
Respond: The OT asset management system is a valuable tool for devising a response strategy that doesn’t do more harm than good. It informs about system dependencies that need to be observed when taking devices offline.
Recover: The OT asset management system is a great place to store system recovery plans. System recovery was already covered earlier, as it is not limited to causes within the cyber security realm.
A different level of visibility: The big picture, als painted by the numbers
You may have heard that an asset management system increases visibility of the installed OT base. This is almost intuitive when thinking about individual PLCs, HMI stations, network switches and so on that the asset owner may not even have known existed before they were automatically identifided by the asset management system. That’s visibility at the micro level.
A totally different level of visibility is achieved at the macro level, where we are no longer looking at individual devices and their configurations, but at the big picture. The OT asset management system allows you to see the totality of OT assets, along with their security vulnerabilities, firmware version spread, obsolete operating systems and so on. It shows hard numbers, and those numbers provide hard insights beyond the fact that a particular PLC might run outdated firmware.
Consider, for example, a well meaning exercise to increase security patching in an organization. A new patch policy suggests that Windows boxes in the OT space should be patched quarterly to mitigate critical vulnerabilities. The OT asset management system clearly shows the results of this effort: In the first patch cycle, a total of 500 patches have been installed on the roughly 100 Windows PCs in a hypothetical plant.
500 patches, that sounds impressive. But when put into context, the picture might change. The OT asset management system also tells us that there’s a backlog of 50.000 vulnerabilities for our PCs that wait to be fixed. (In case you wonder: This number is well below average.) Let’s assume that we don’t need to install 50.000 patches total because some patches mitigate more than one vulnerability. If we only account for 25.000 patches in the backlog, that means it will take over ten years just to clear the backlog, without accounting for new vulnerabilities that pop up during this timeframe. Certainly not what was intended.
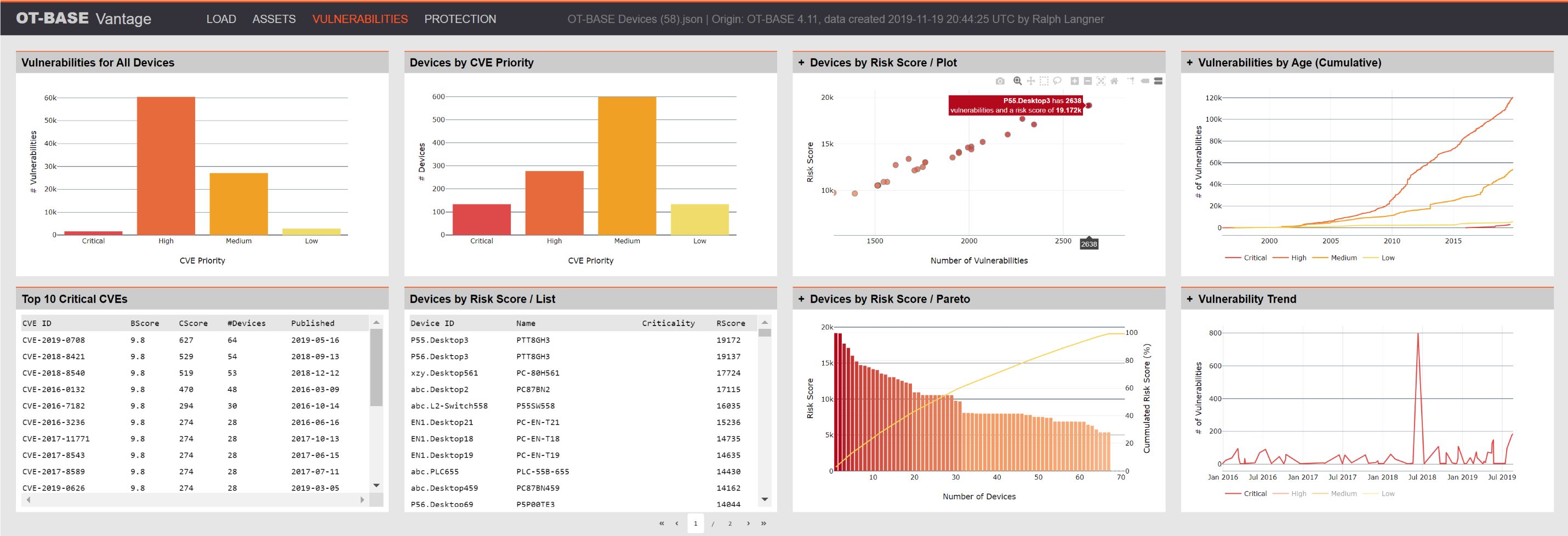
Talking about new vulnerabilities: The asset management system may also show that 80% of computers are running Windows 7 and other operating system versions beyond end-of-support, suggesting that we have a far bigger problem ahead of us which will not be addressed by the new patching initiative.
Bottom line: The sober numbers presented by the OT asset management system help to distinguish real progress from security theater. Considering the fact that OT security efforts always undergo extra scrutiny in respect to their business value, the metrics that can be pulled from the OT asset management system go a long way in developing and executing a sustainable OT security strategy.
Conclusion
OT asset management covers multiple use cases that are essential for running, maintaining, designing, and securing the modern industrial enterprise. This is hardly surprising in face of the digital transition as plant environments become more complex, more connected, more vulnerable, and less transparent. For complex plant environments with thousands of OT assets, the use of an OT asset management system is a necessity.
Automatic asset discovery is successfully in use for many years, and there is no excuse for even trying to gather asset data manually. There is an ongoing debate about “passive” vs. “active” approaches to discovery, however for large OT installations with hundreds of networks, “active” is the only economically viable approach to pursue as it doesn’t require to install discovery appliances in every subnet.
The OT asset management system covers several different use cases in engineering and maintenance and is also the foundation of a sustainable OT security program.
Watch this video to see how it all comes together
