Guess what, the biggest problem in OT security isn’t the ever changing threat landscape. It’s the inefficiency of popular OT security strategies and processes. Why inefficient? Simply because they don’t pay any long-term dividends. Your OT threat detection efforts don’t yield any long-term benefits; they “burn off” right here and right now. The SIEM alert that you just processed doesn’t prevent future alerts.
Similar with patch management. The patches that you install today don’t eliminate the need to apply further patches for the same product in the future.
So the two most common OT security tactics – threat detection and patching – are inefficient simply because they don’t deliver any long-term gains in security posture. They are not investments in the company’s OT security future, with measurable reductions of the attack surface. It’s like being caught in that proverbial hamster wheel. New vulnerabilities and threats keep coming, no matter how fast you run.

Characteristics of compound OT security methods
In order to set the company up for long-term gains in OT security posture, other tactics are needed. Such tactics need to have the following characteristics:
- Lasting, progressive effect: A solved problem stays solved. The effort required to solve other problems in the same domain is reduced. It gets easier as you go.
- Scalability: Every single issue within the domain doesn’t need to be addressed individually; it is possible to tackle multiple issues in one go (“kill multiple birds with one stone”).
- Combinatorial multiplication effects: The combination of tactics yields multiplied, rather than additive results.
We’ll discuss what this means for three specific OT security tactics: Network segregation, system hardening, and configuration management.
How to do network segregation right
Network segregation may well be the most important OT security strategy, and certainly the strategy that every organization arrives at sooner or later in their OT security journey. Once you have figured out that no patching will make your PLCs, RTUs, VFDs etc. secure (because they are insecure by design), you are bound to implement the only logical solution: Network security.
After having properly segmented your network, you can pretty much relax your patching regime because if no malicious traffic can reach a vulnerable endpoint, the vulnerabilities cause less concern. Good!
The OTbase OT asset management software generates network topology as associated with work cells — an ideal foundation for zoning, and criticality determination
The real challenge for network segregation is where and how to draw the boundaries. Few organizations have a good idea about required network traffic, and how to segment properly. Spoiler alert: The Purdue model won’t help you here. What is required is a solid understanding of the production process and its segmentation into work cells, along with their interdependencies. The OTbase OT asset management software provides this understanding and will guide you through your micro-segmentation.
System hardening: Eliminating vulnerabilities by the thousands
Hardening basically means that you remove system characteristics that aren’t necessary but can only cause grief.
A perfect example is the presence of software products that don’t have any business on the plant floor but can often be found anyway – because they were part of the standard install, or because they have been left over by a contractor or automation vendor after commissioning.
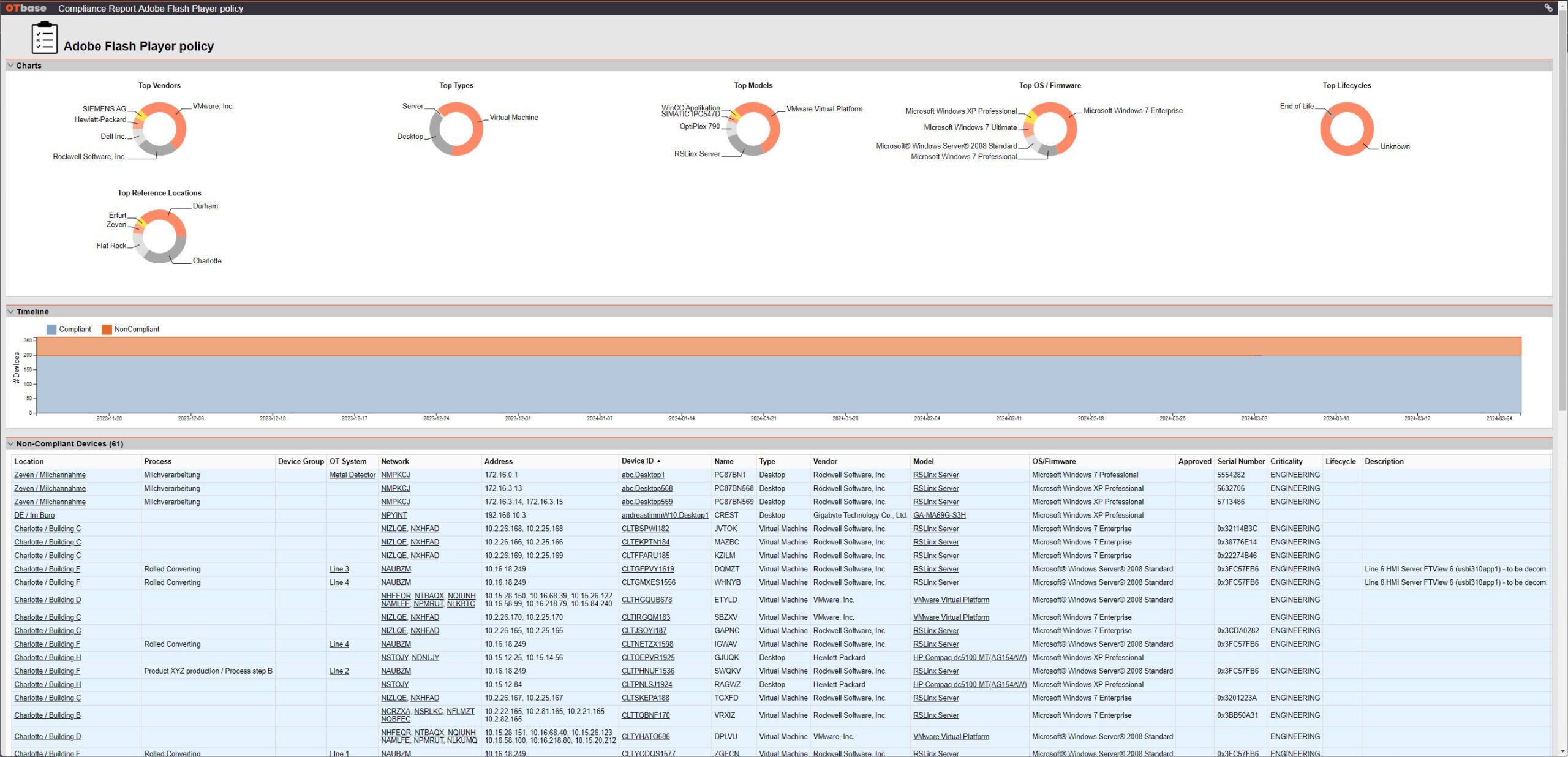
Think about Adobe Flash Player. This product comes with hundreds of vulnerabilities, and at the same time you will have trouble finding an industrial application that would actually depend on it. Think about outdated office software, outdated web browsers, remote access products such as VNC or Teamviewer. All of these carry a lot of opportunities for cyber threats.
OTbase exposes those software products that contribute most to the attack surface, providing a basis for system hardening
A related problem is the use of insecure protocols. Examples include Telnet, SNMPv1, SNMPv2, or HTTP. Disabling the respective services and replacing them with secure alternatives (if even necessary) goes a long way.
Configuration management
System hardening already goes a long way as it allows you to get rid of so many vulnerabilities at once for a given system. But it gets even better when combined with standard configuration policies that can be audited automatically. Such is made possible by configuration management.
Assume, as an example, that your organization has decided to prohibit the use of Flash Player, Windows 7, Teamviewer, Telnet, you name it. The real kicker is if you (and auditors as well) can see instantly which systems are compliant, and which ones are not. Effortless. No need for auditors to come on site and do walk-down inspections. And every new system will be checked for compliance even before commissioning, making sure that the bad stuff is removed before it creates cyber risk.
Configuration management will also inform you about any random deviations from approved configurations (a.k.a. configuration drift), which happens every now and then when contractors change configurations without telling asset owners. This aspect is usually referred to as configuration integrity assurance.
A policy profile exposes non-compliant devices along with a timeline that lets you track progress towards achieving compliance
The OTbase OT asset management software includes these capabilities. Compliance audits take seconds, rather than days or weeks. Even better, every system owner knows at any point in time if their configuration is compliant or not, or if it has drifted away from approved system states. In a way one could say that configuration management is the pinnacle of OT asset management as it allows the asset owner to assure that OT configurations down to the most minute detail are conformant with design goals — design goals that reflect cyber security aspirations, business continuity requirements, and maintainability objectives.
Conclusion
Let’s revisit our initial premise.
Consider an environment where you have implemented the three approaches explained in this article: Network segregation, system hardening, and configuration management. How would this affect your network anomaly detection and patching efforts?
The answer is obvious: Efforts in both areas will go down. You don’t need to constantly and timely patch systems that are located in well protected network zones. You don’t need to patch software that you have removed from your systems (hardening). You won’t spend as much time on your anomaly detection because as a result of network segregation and system hardening, potentially malicious network traffic is reduced dramatically, and so is the number of alerts. And processing the remaining alerts is simplified by the contextualization provided by the OT asset management system.
Overall you will see measurable improvements in your OT security posture, along with a good idea on how to build on the initial success. You are collecting the dividend of compound OT security gains.
To learn more about the OTbase OT asset management software, check out https://langner.com.