Enterprise-grade OT asset management software
OTbase is the gold standard for large-scale OT asset management. It inventories OT devices from PLCs over network switches to sensors and actuators and integrates nicely with your existing tools and platforms. OTbase scales well beyond 500k devices and is used by Global Manufacturing and Big Oil.
Want to drive the digital transformation in OT? Then get away from Excel as quickly as possible.
The digital transformation in OT is a huge endeavour in mastering change of complex digital infrastructures. Excel is not the tool to make it happen. Step up to a platform that was specifically designed to help large enterprises move toward secure and resilient OT networks: The OTbase OT asset management software. Designed by the team that cracked Stuxnet.
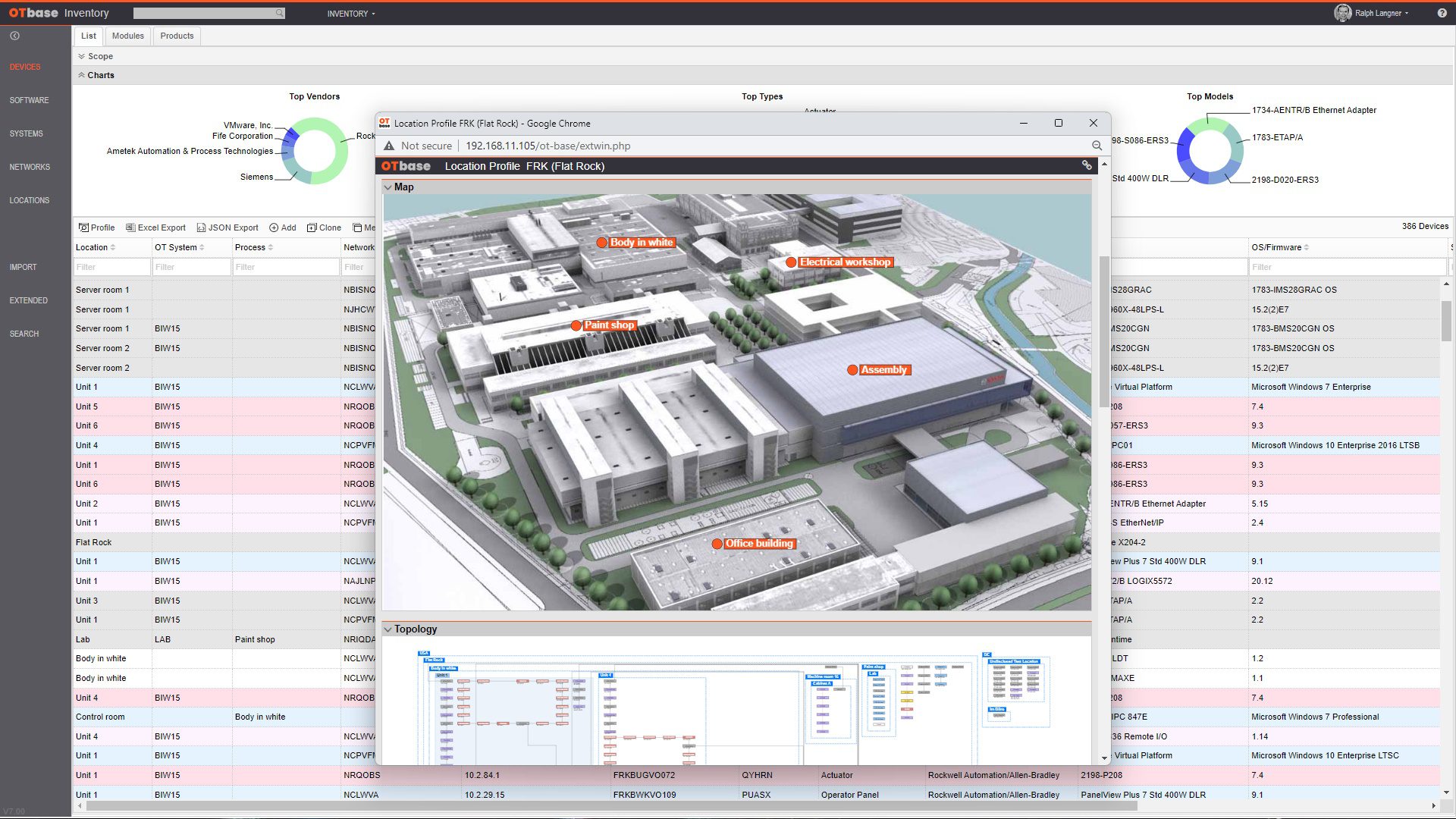
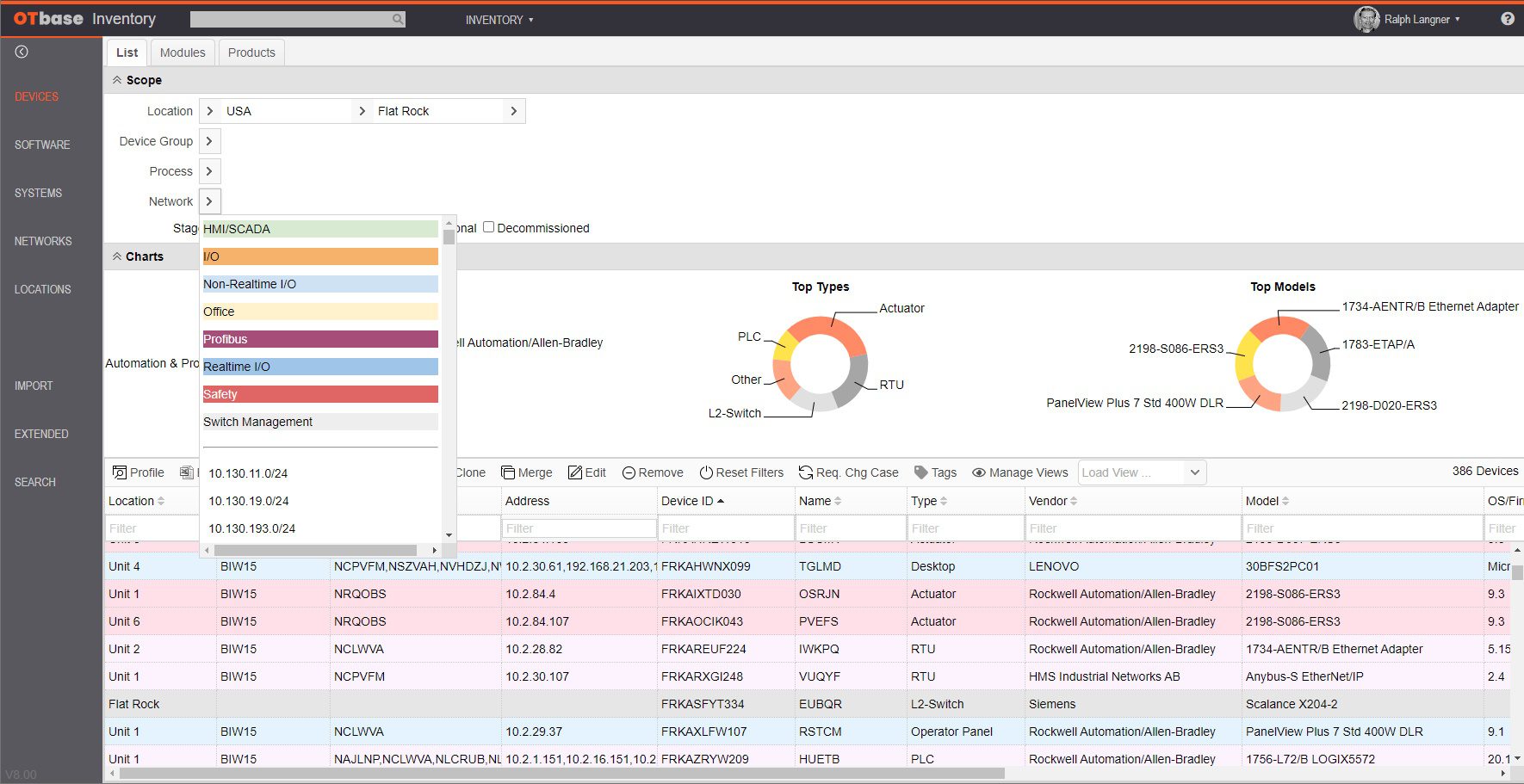
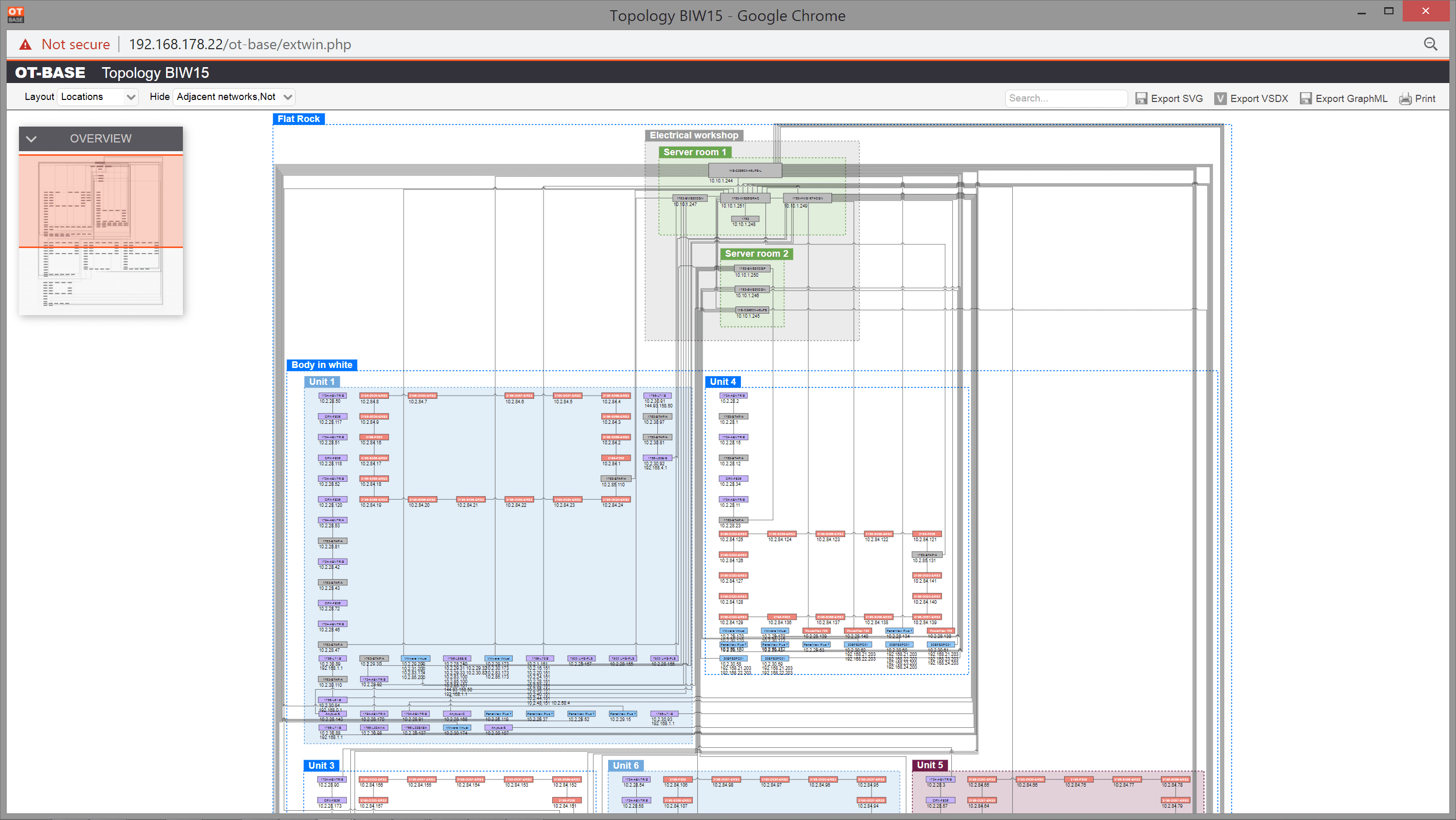
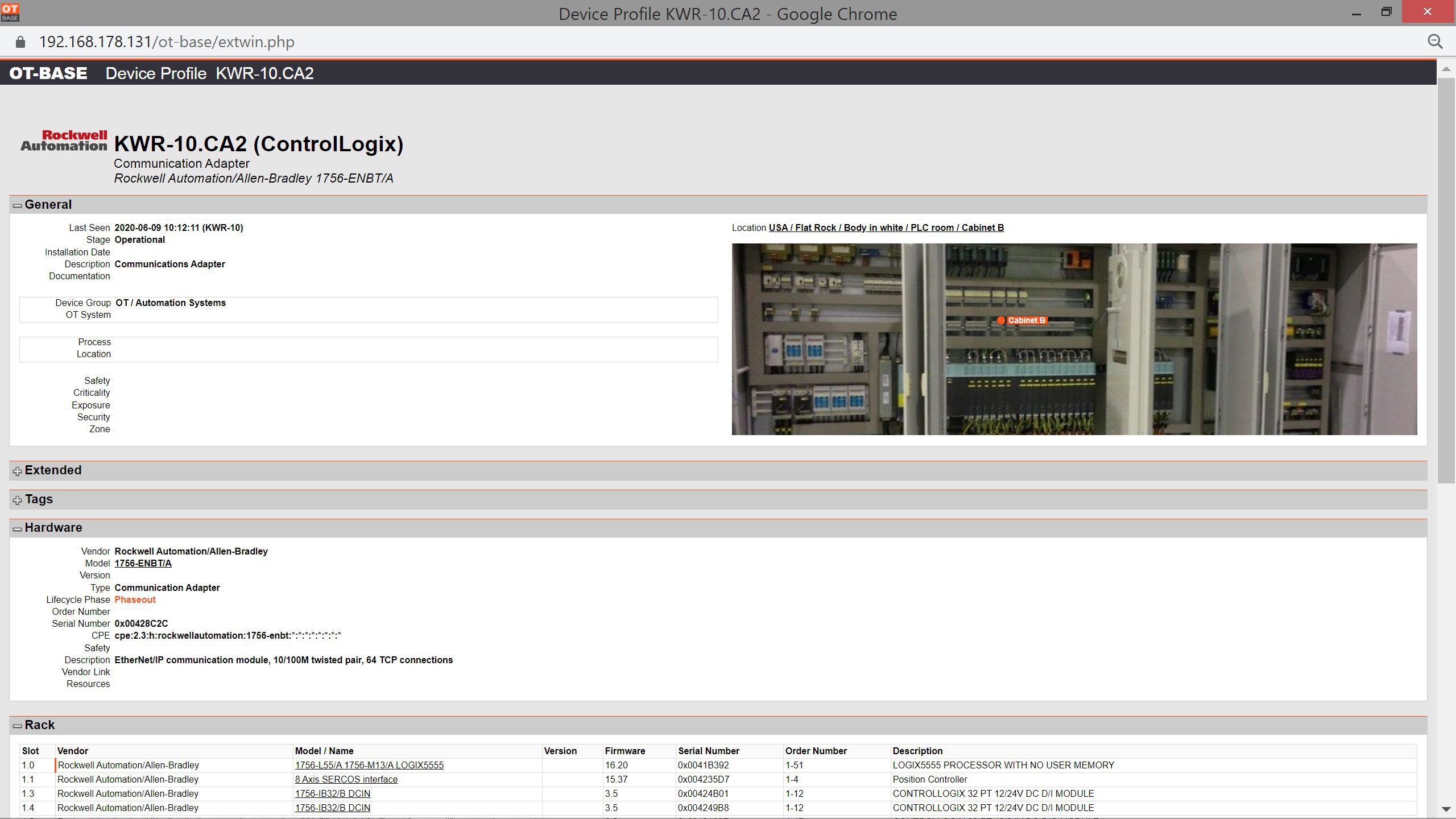
Create a global OT asset inventory
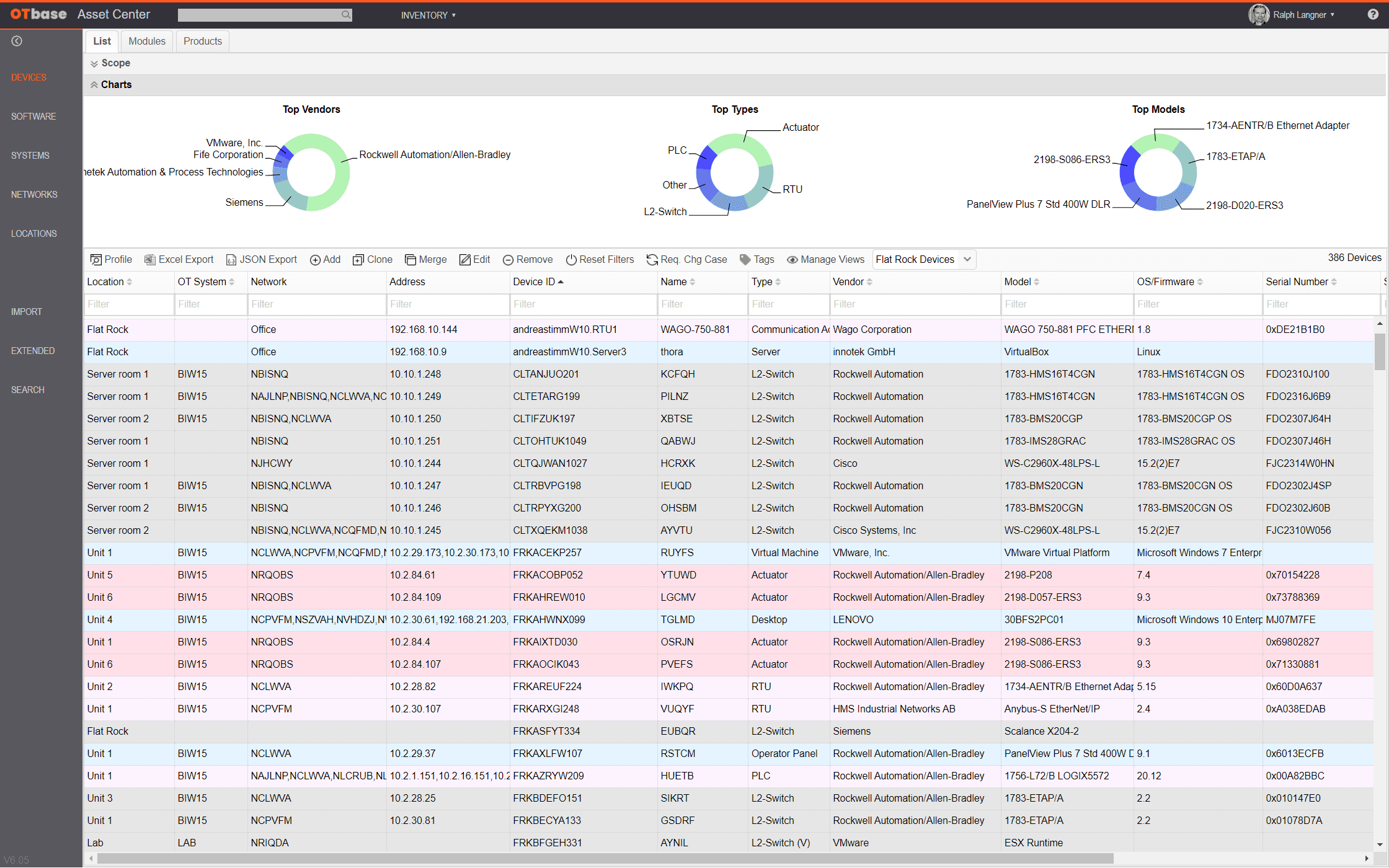
OTbase automatically inventories your OT devices, networks, and software. You don’t need to deploy hardware sensors. Daily updates ensure that you don’t miss configuration changes and new devices on the network.
Learn more >
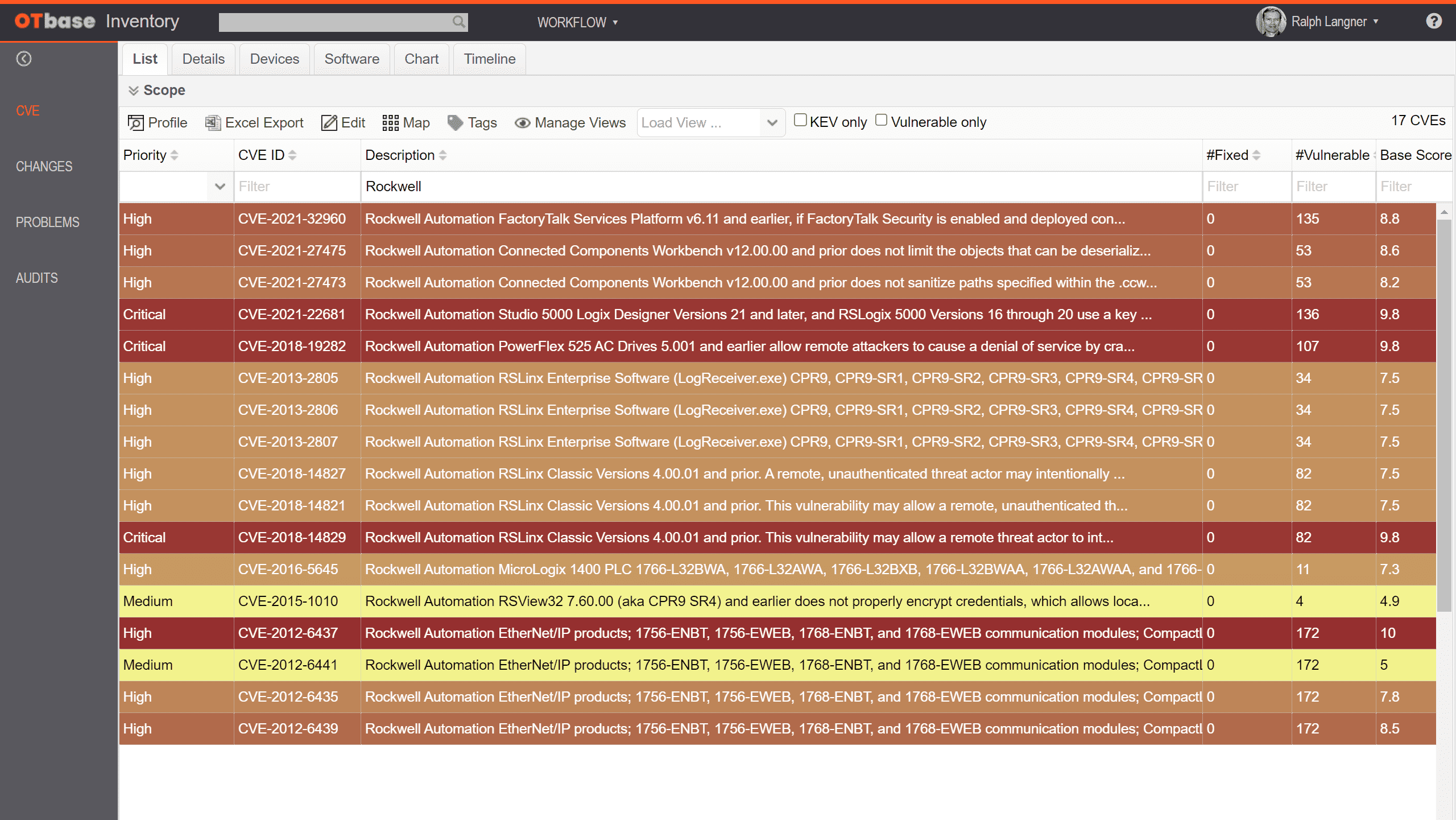
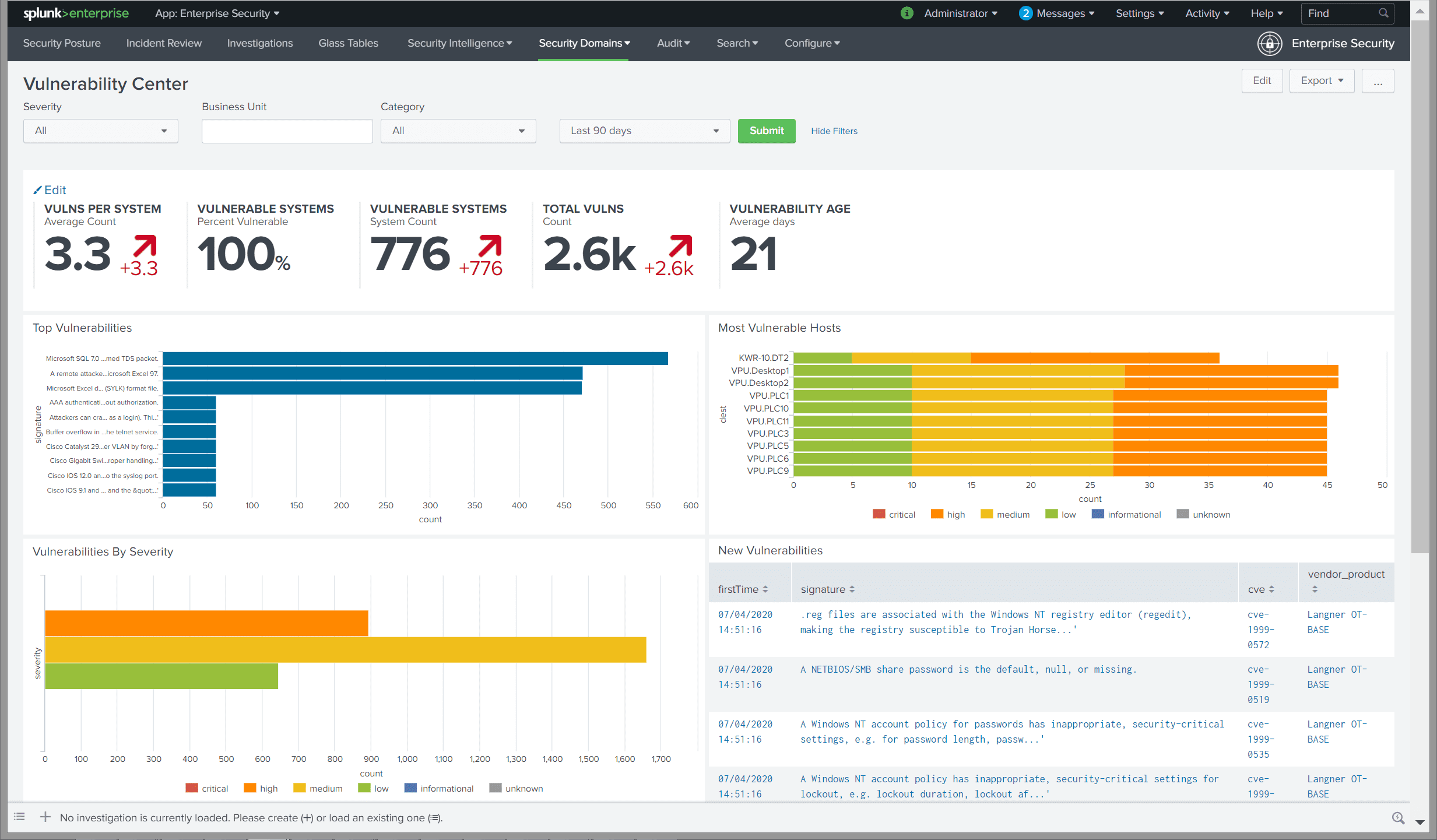
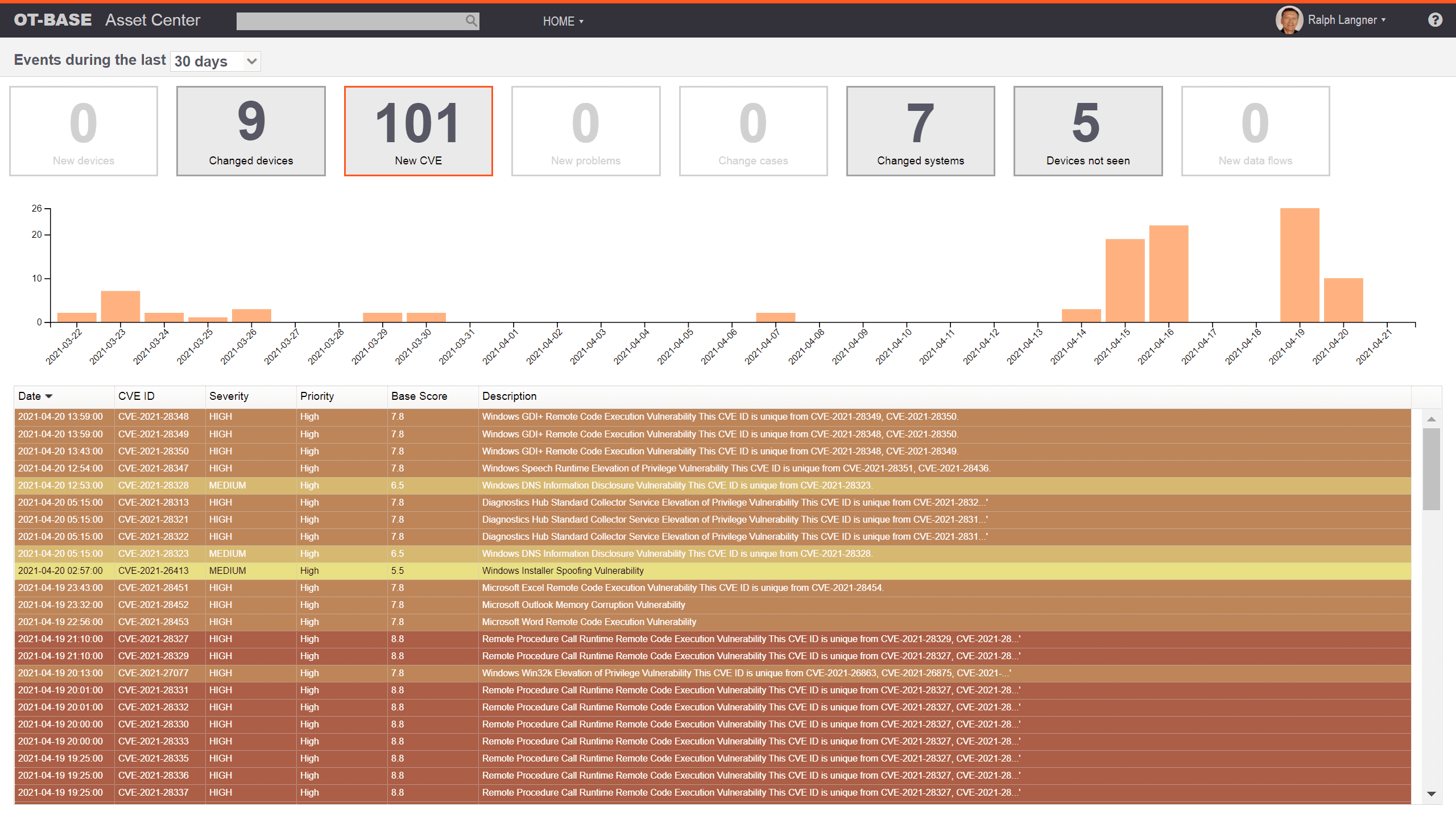
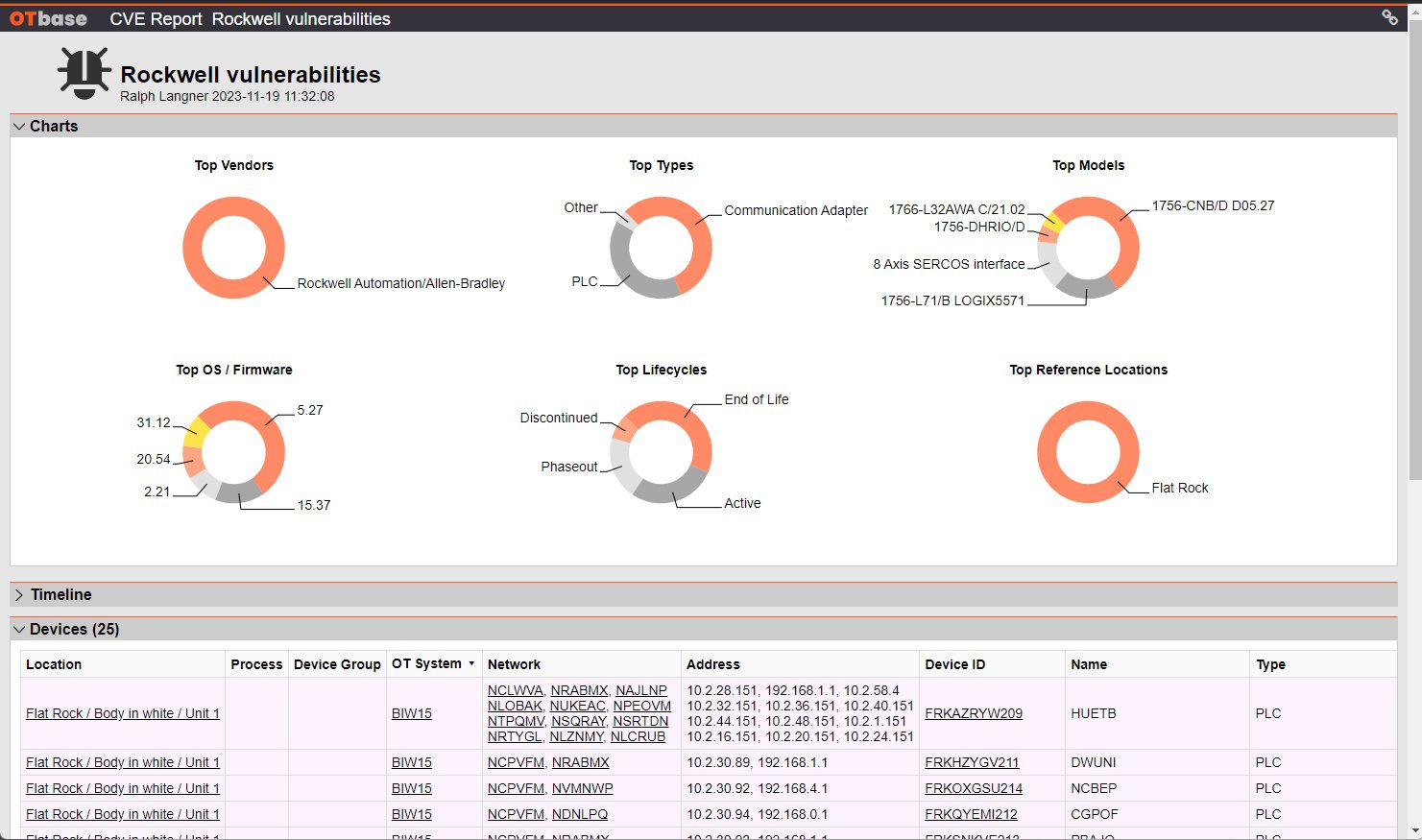
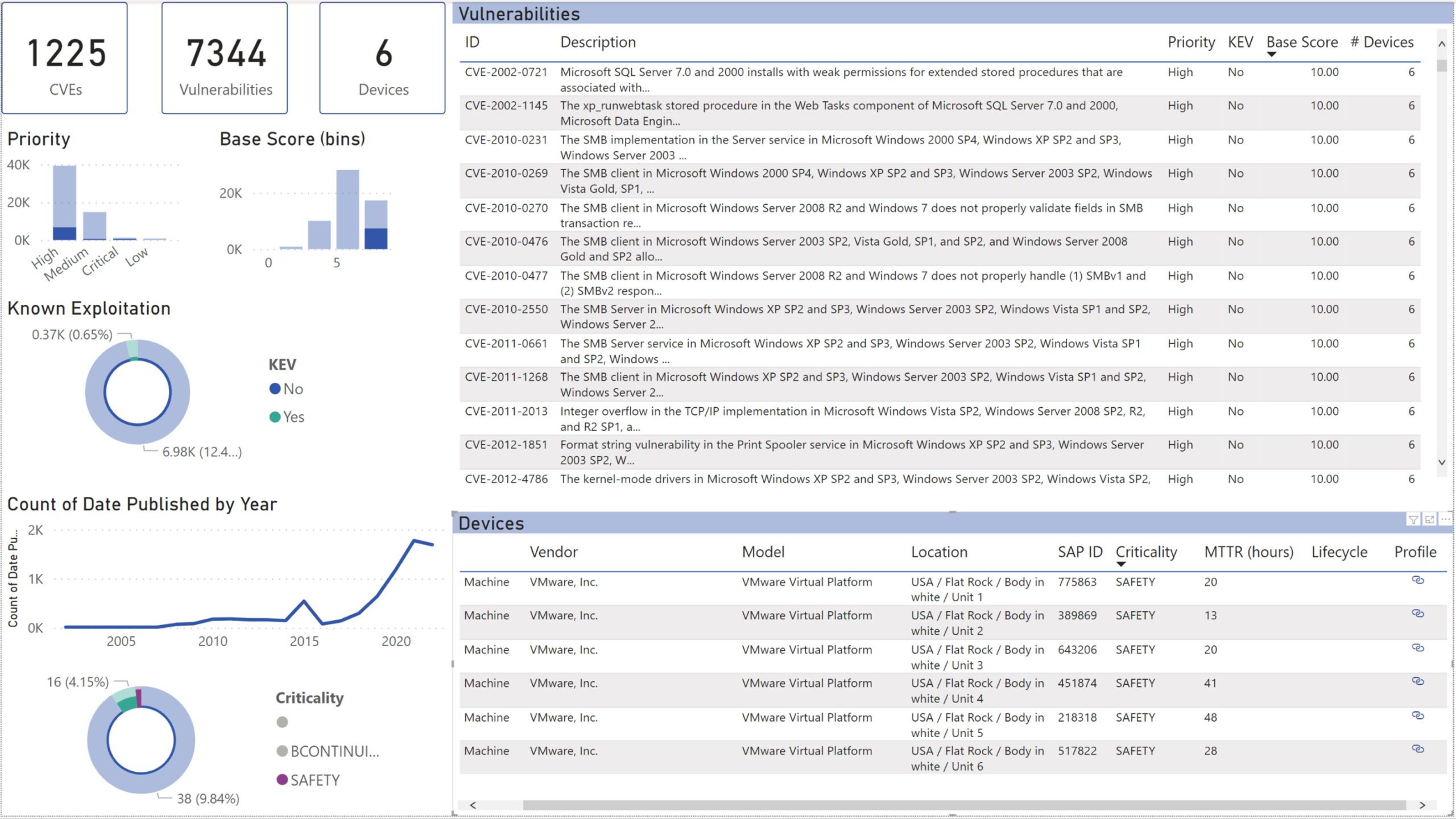
Identify and mitigate cyber security vulnerabilities
See all CVEs that affect your installed base without ever executing a “vulnerability scan”. OTbase does all the work for you behind the scenes. Use prioritization to build a vulnerability management strategy that works best for you.
Learn more >
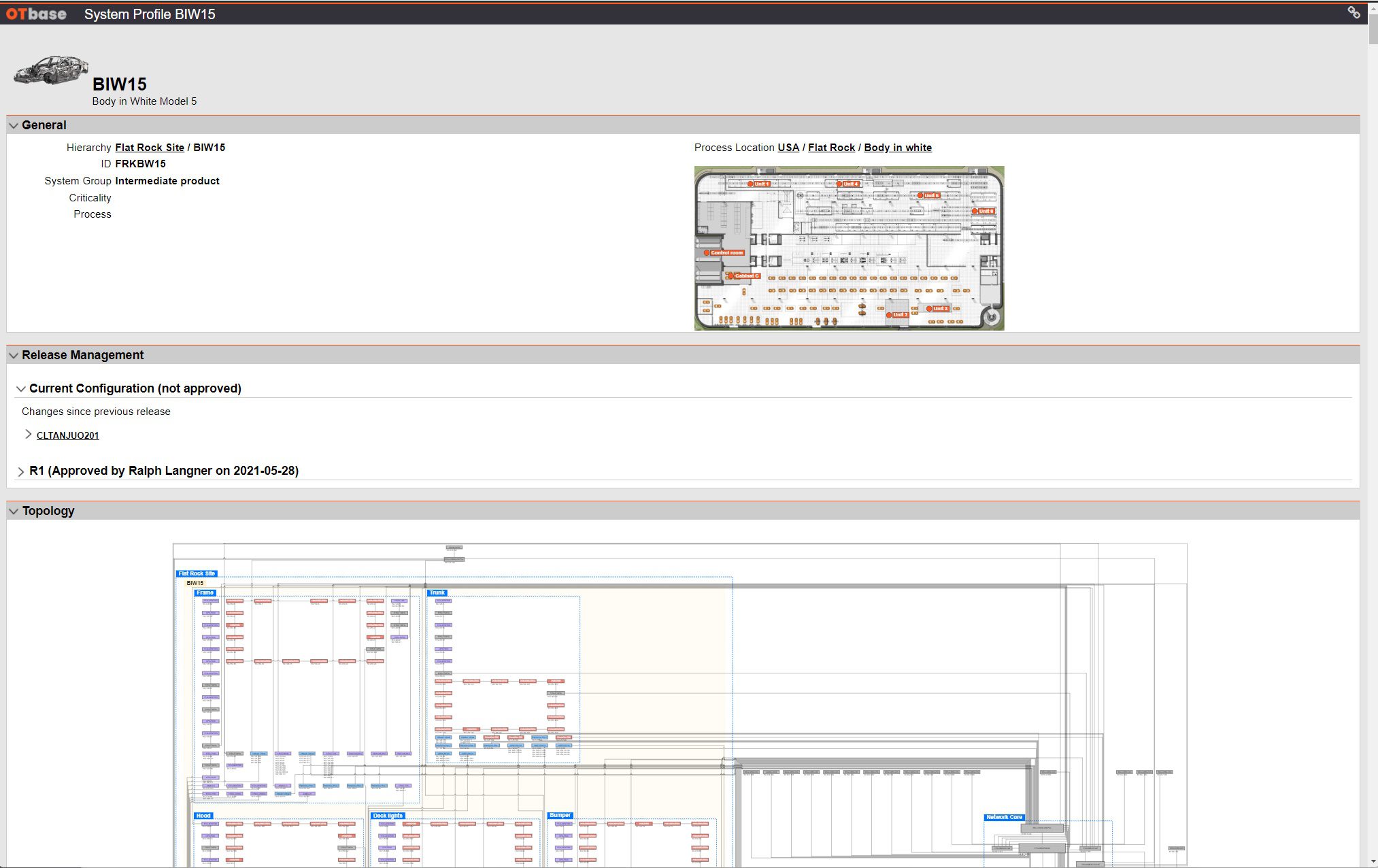
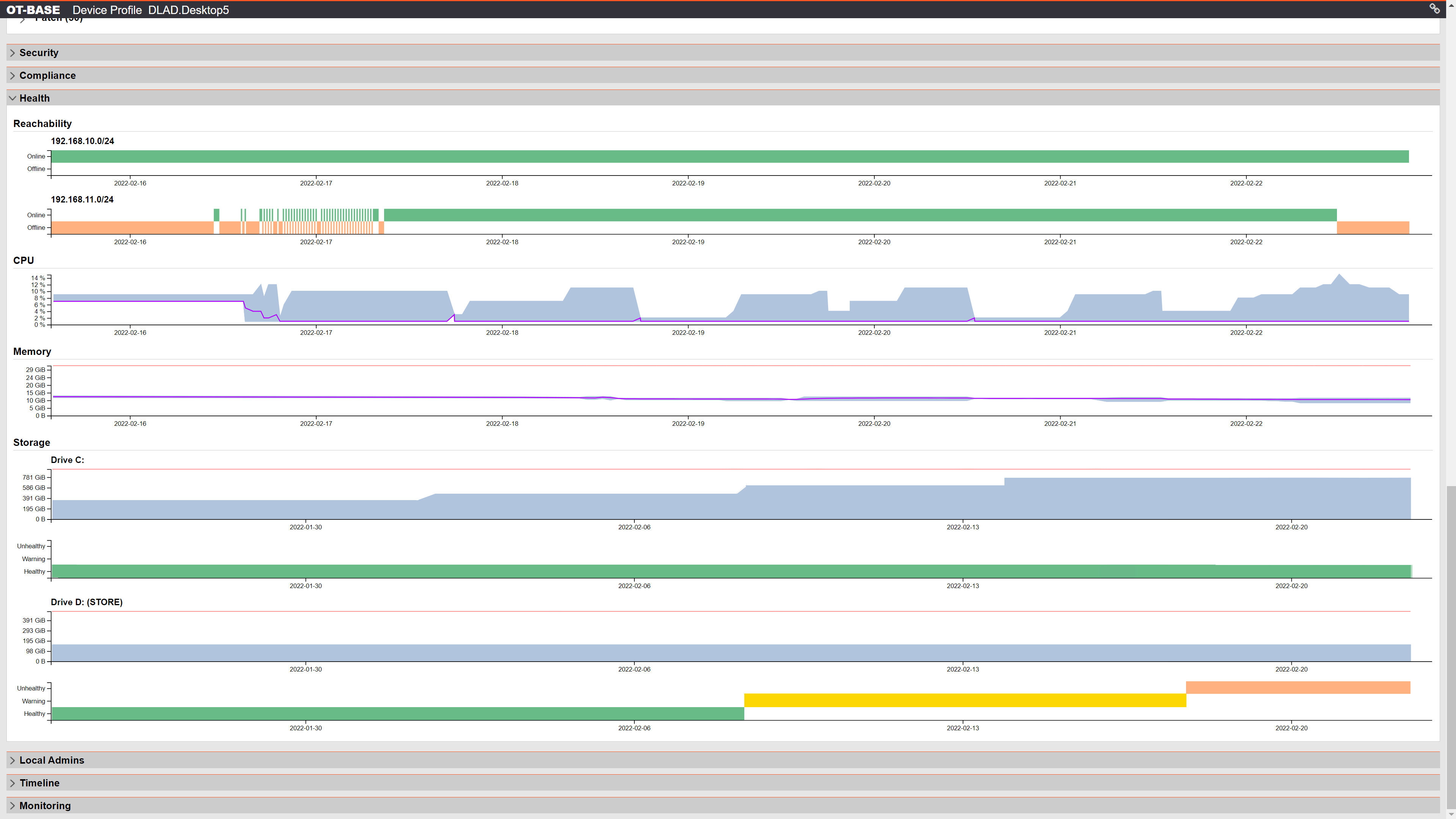
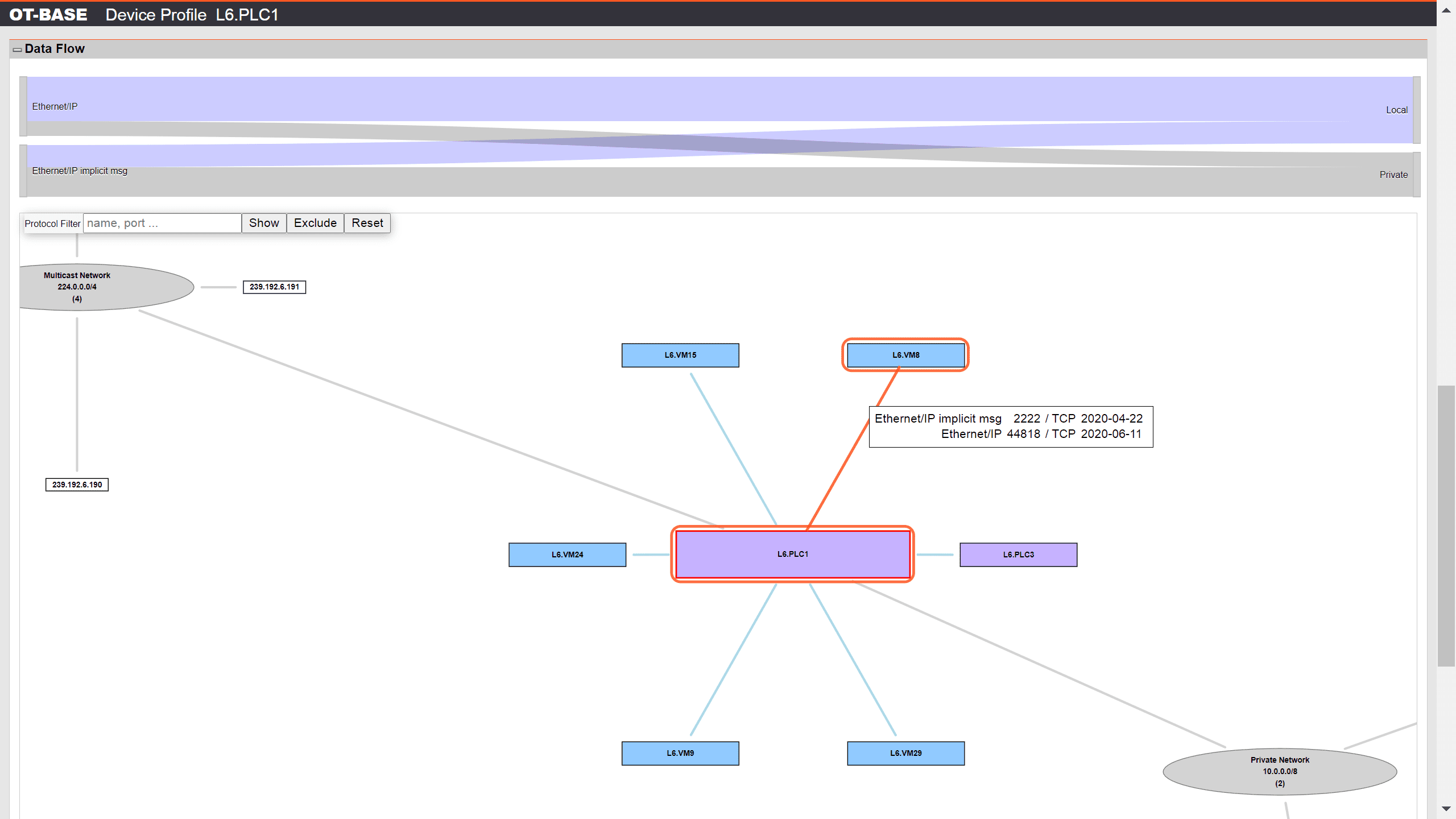
Identify, plan, and document configuration change
OTbase detects configuration change automatically and maintains a timeline for every device. It also comes with workflows for change management, and configuration integrity monitoring.
Learn more >
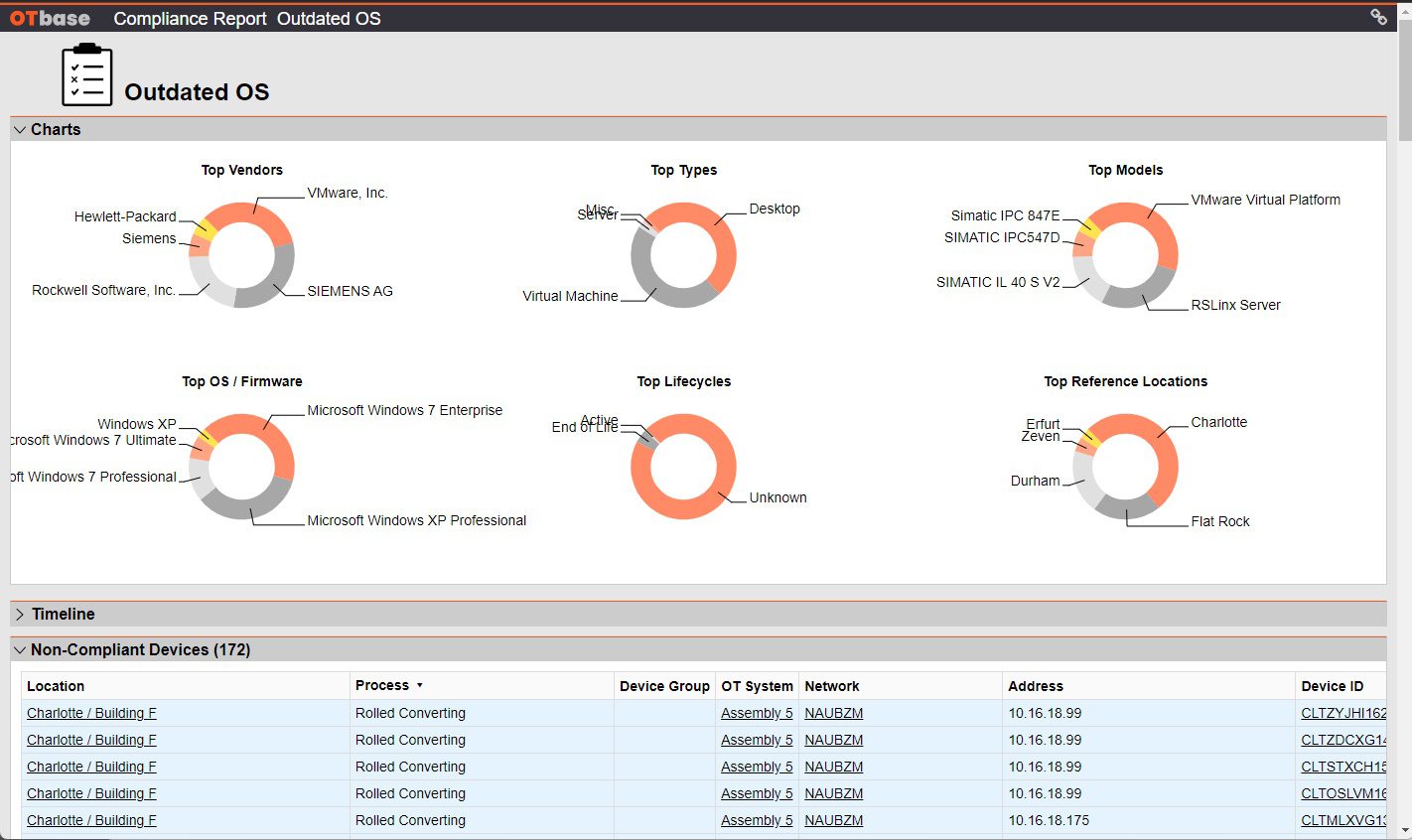
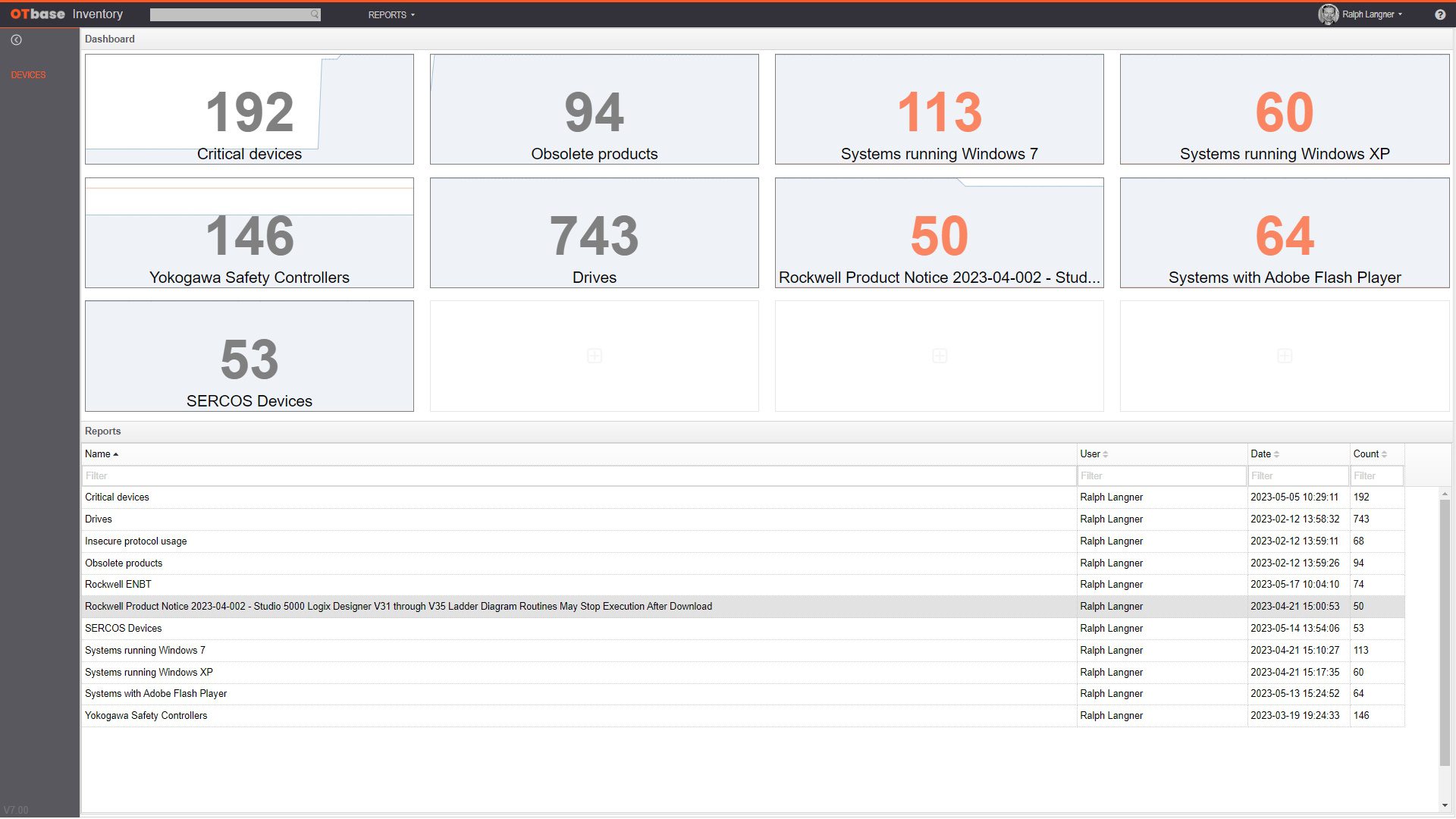
Identify obsolete OT products that can no longer be replaced
See all OT products in your inventory that are end of life, or will soon be. Furnish a replacement strategy before running into substantial business continuity risk.
Learn more >
Capture valuable engineering knowledge from retiring staff
Senior engineers who have designed critical parts of your IT infrastructure will retire soon. OTbase allows you to capture their knowledge and make it available to the next generation.
Learn more >
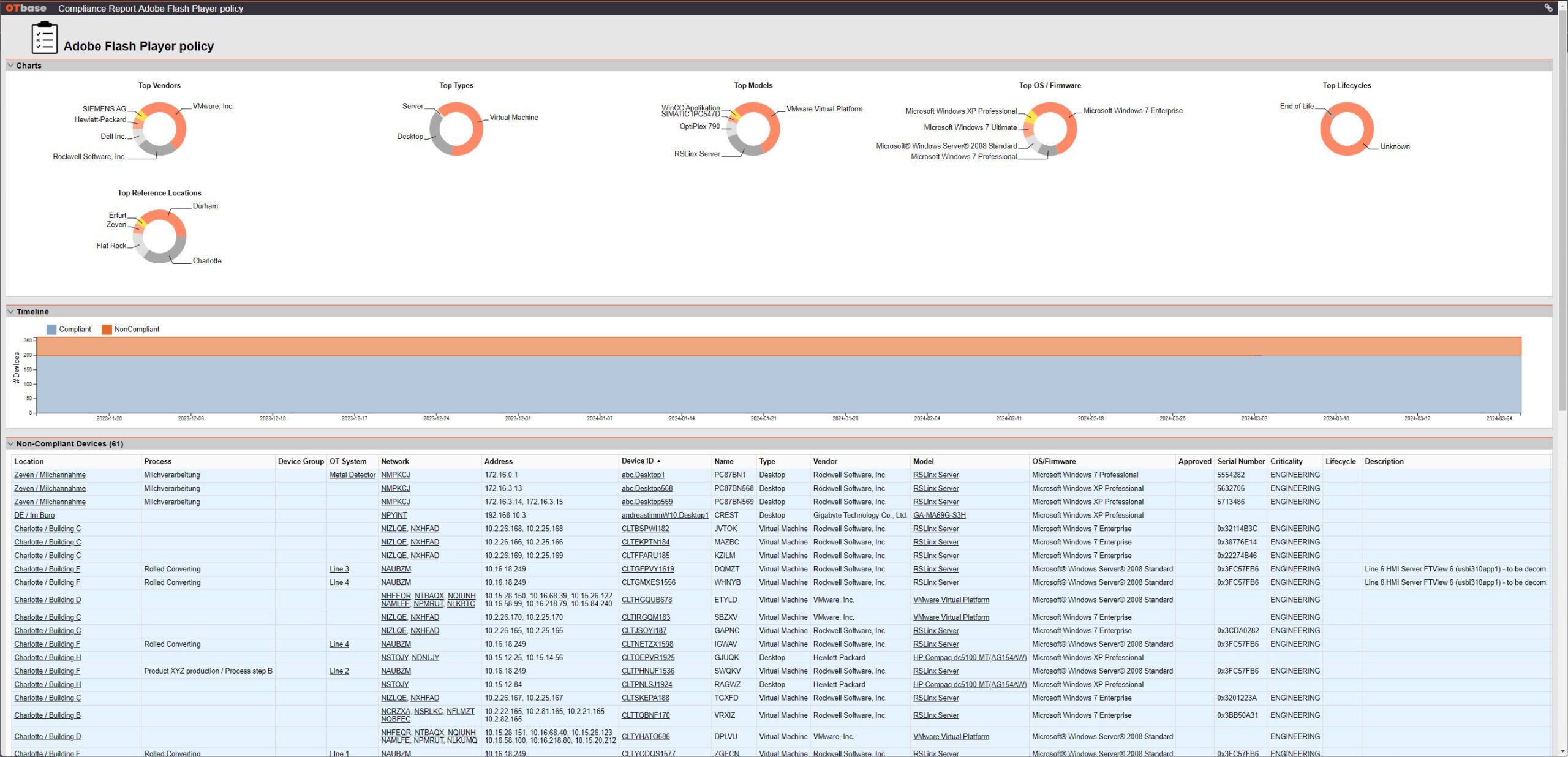
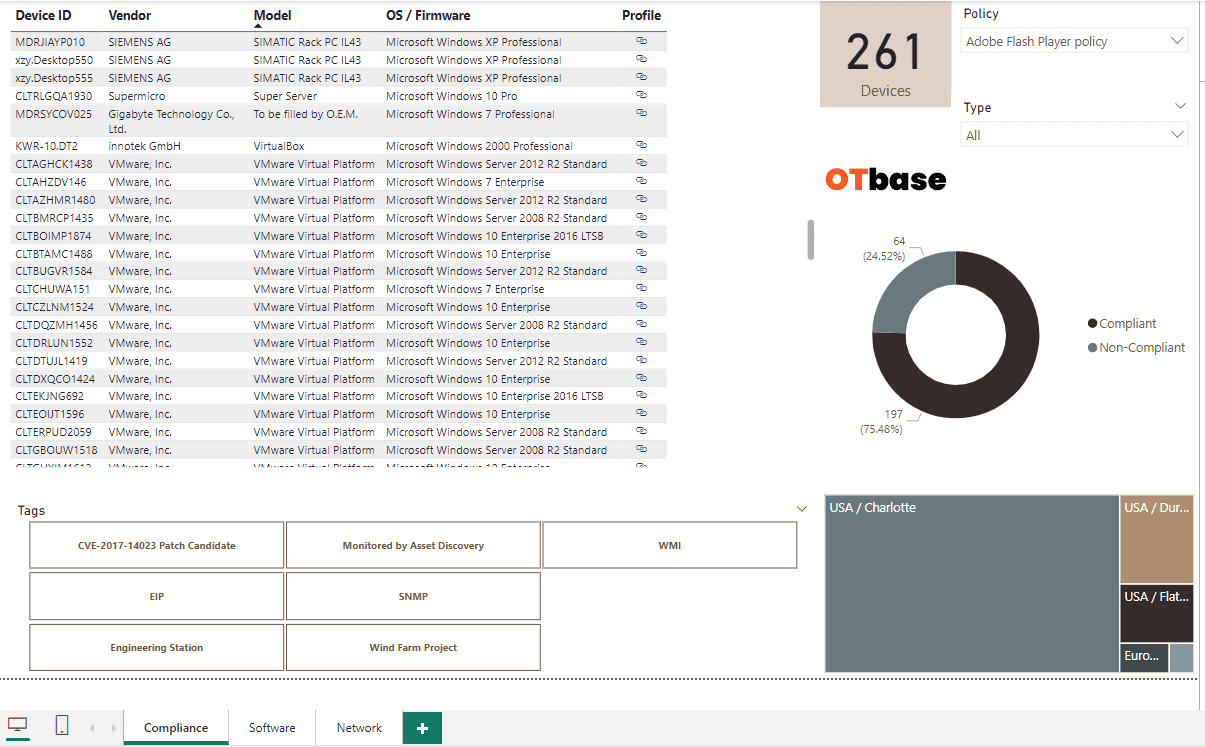
Establish corporate OT configuration policies with continuous compliance audits
Standardization is the key to efficiency. OTbase lets you set up standard configuration policies, such as required or prohibited software products, and execute automatic audits. No more walk-down inspections needed.
Learn more >
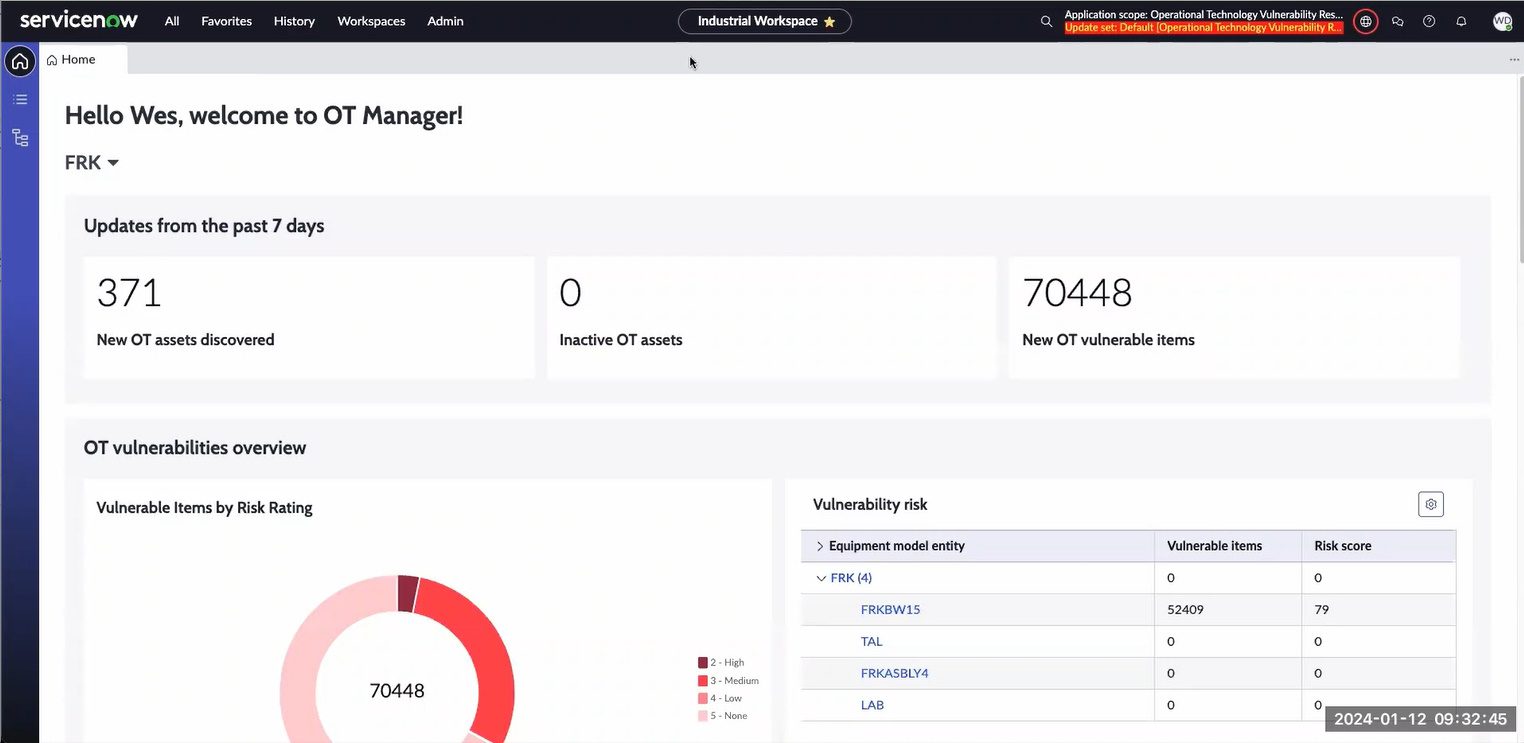
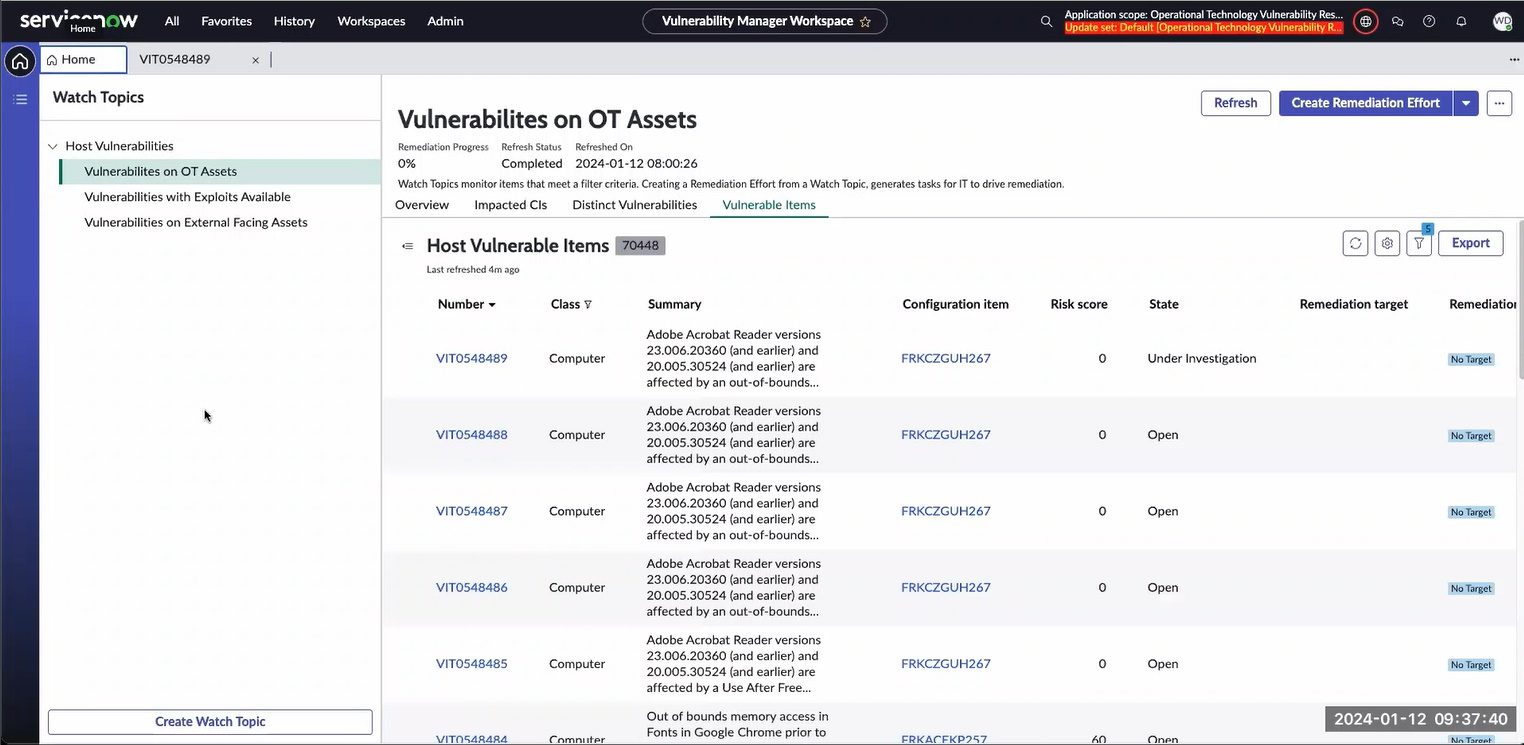
Provide essential contextual information for your SIEM
Your SIEM picks up alerts from OT systems, but you don’t know what to do with it because there is no system context? OTbase changes this. Your analysts get all the information they need for an informed assessment.
Learn more >
Show everyone that you are on top of things with awesome reports
OTbase gives you all the reports you need, and more. Choose between self-updatinig native reports, or use Power BI to create CISO dashboards in a couple of hours.
Learn more >
Once you’ve seen it
you will never want to go back.
When your company’s success, and your team’s efficiency, depend on how well you understand and manage tens of thousands of digital OT devices, you need a software platform that was specifically designed to do the job: The OTbase OT asset management system with engineering integration. Look at the screen shots and product videos and you will understand why OTbase is the prime choice for large enterprises.
Get rid of your Excel tables that are an excuse for an asset inventory
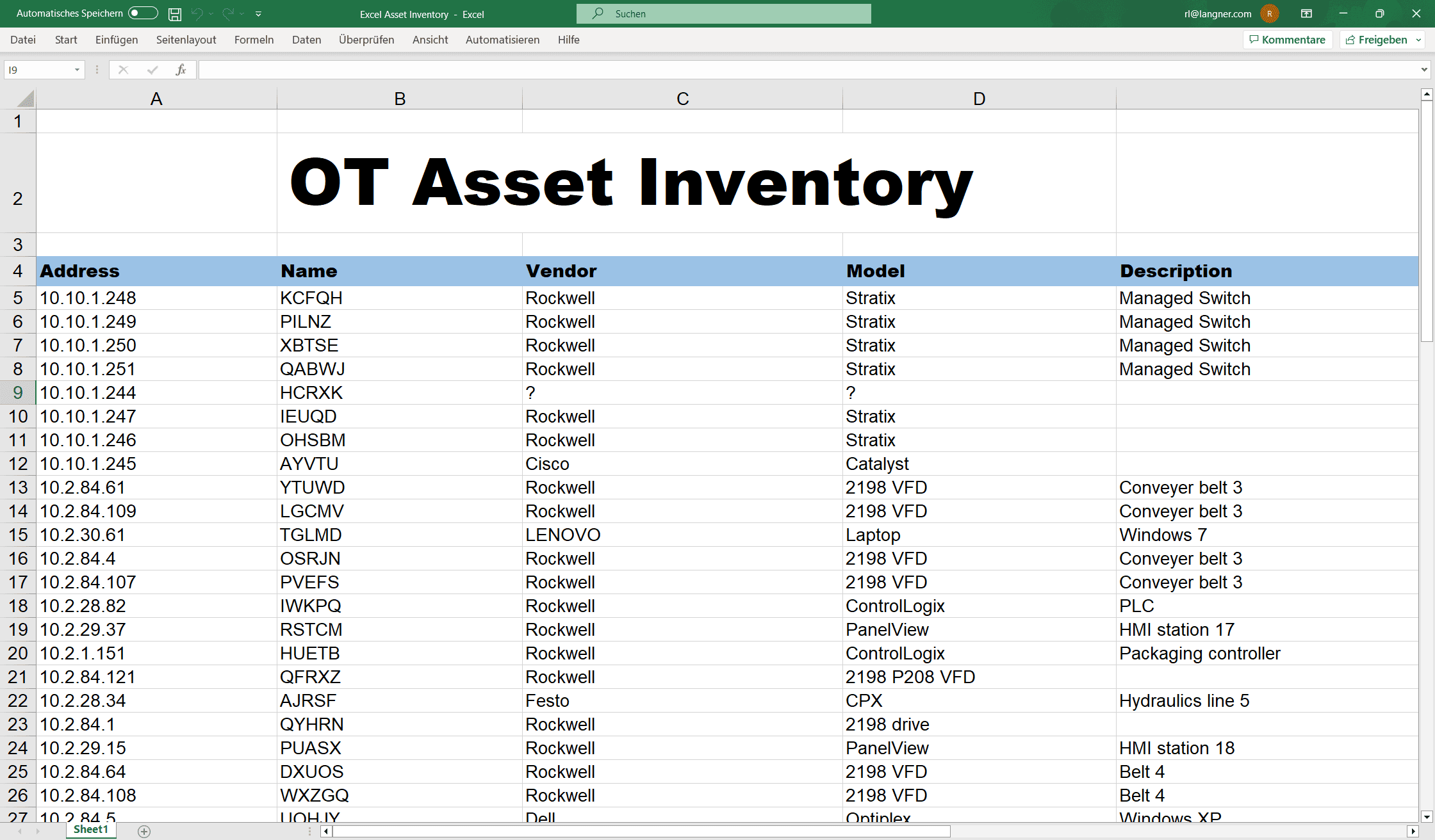
Manually created OT asset inventories in Excel are a waste of time. They are incomplete, inaccurate, and outdated before the end of the month.
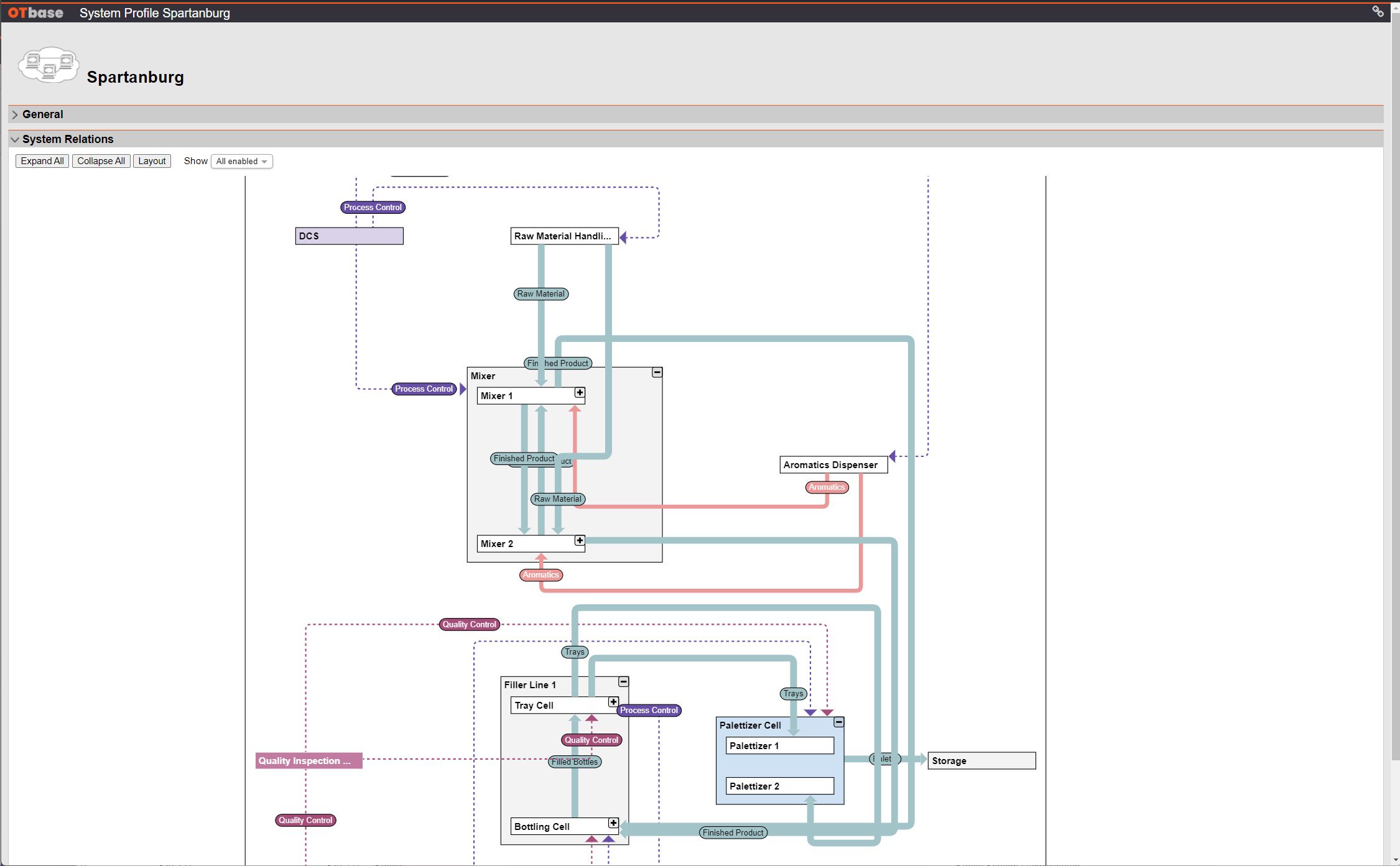
OTbase creates your OT asset inventory automatically and keeps it up to date effortlessly. And it comes with a wealth of add-on functionality such as vulnerability management, network topology, and more.
In this day and age, if you still try to keep track of your OT assets in an Excel table, you know fairly well that you’re doing it wrong. It’s simply impossible to manually collect and update thousands of OT devices along with their serial numbers, I/O modules, firmware versions.
This is where OTbase comes in. It automatically builds your OT asset inventory and allows for easy data enrichment using your existing metadata. All OT asset information is then stored in a global database on your enterprise network that is fully protected by granular access control.
Best of all, OTbase automatically adds vulnerability data and vendor product metadata such as product lifecycle status and current firmware version. The resulting data set can easily be shared with other tools such as Power BI, ServiceNow, or Splunk.
The first OT tool that wasn’t designed with hackers in mind, but with you — the user
There are around 30 products in the “ICS Detection” category, but OT-BASE isn’t one of them. You may have a hard time understanding how one ICS Detection product is different from the next, but it’s easy to see how OT-BASE is different from all of those.
OTbase is a pure-play OT asset management system. It doesn’t detect cyber-physical attacks that might happen once per decade. It makes users more productive — users in engineering, auditing, cyber security, plant planning, and related fields.
To learn more about why OT asset management is a product category in its own right, please check out this blog post.

Enterprise-grade
OT asset management software