To give you an idea how carefully the man-in-the-middle attack on the 417 is crafted, let’s focus on one specific detail. Just one out of many. (Note: You probably won’t be able to understand the following without very good knowledge of controller architecture.)
As outlined before, a controller holds a memory image of the physical inputs and physical outputs. This is what the controller program, or ladder logic, usually operates on. Stuxnet disables automatic updates of physical and logical I/Os by the execution environment, exploiting a legitimate configuration setting. During the attack, it feeds fake input data to the input process image. (By the way, did you know that the input process image was not read-only? As a matter of fact, it can even be manipulated via the network, but that’s another story, and not exploited by Stuxnet.)
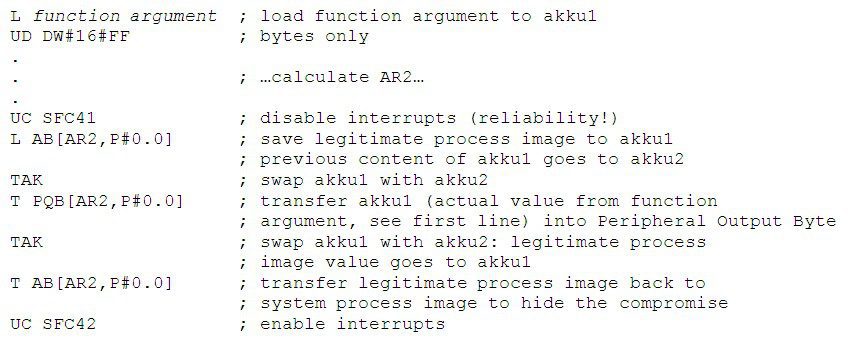
Now here’s the catch. During the attack, Stuxnet writes directly to physical outputs. If you do that on a S7-417, the execution environment will automatically update the output process image thereafter. In theory, this would enable the legitimate program to sniff something was wrong. However, the attackers took care about that. They are not rookies. They simply SAVE the legitimate output process image before going to physical, and RESTORE the legitimate process image afterwards; all this with interrupts disabled for reliable operation. Rock solid engineering job.
Excerpt from the original attack code in FC 6076, comments added by us: